Microsoft Active Directory Security Part 2: Decoding Active Directory Attack Paths to High-Value Targets
In a previous blog, we provided an overview of the (unfortunately quite complex) Active Directory Attack Surface. In Part 2 of this series, we’ll explore how attackers and malicious users plan their movement and traverse Active Directory attack paths once they have discovered AD vulnerabilities, misconfigurations, and other weaknesses that they can exploit.
What Is the Microsoft Active Directory Environment?
Microsoft Active Directory provides LDAP-based directory services to a very large number of enterprises. The Active Directory environment consists of all accounts, devices, groups, applications, and other objects that are managed by Active Directory. Enterprises typically have hundreds or thousands of these objects. In their quest to compromise the Domain Controllers (running Microsoft Windows Server) or any other target in the network, attackers can follow a route that spans any combination of these objects.
The Active Directory environment encompasses both on-premises Microsoft Active Directory and Microsoft Azure Active Directory.
Identity Protection is often used as a synonym for Active Directory Protection. However, Identity Protection is a wider term that covers various areas of enterprise network security. Securing Active Directory is just one of the aspects of Identity Protection.
What Is the Graphical View of Active Directory?
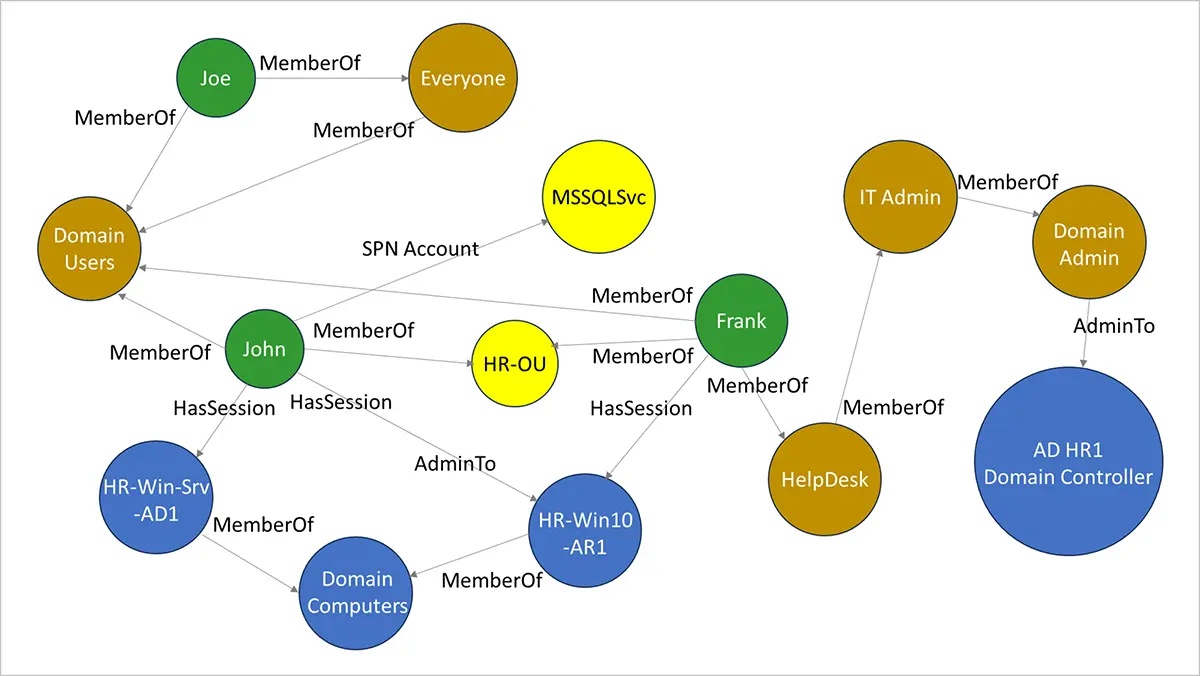
Adversaries look at Active Directory as a graph, not as a relational database of Active Directory users, computers, and groups. Figure 1 shows an example to illustrate how the Active Directory ecosystem is viewed as a graph. Active Directory manages several objects, for example, users, computers, groups, ACEs, and GPOs. Users John, Frank, and Joe are members of various groups, for example, Domain Users, Everyone, Helpdesk, IT Admin, and Domain Admin.
What Is the Initial Step in an AD Attack?
In the example shown in Figure 1, user John has admin access to HR-Win10-AR-1 (a Microsoft Windows 10 computer). He also has sessions on HR-Win-Srv-AD1 (a Microsoft Windows Server computer) and HR-Win10-AR-1. Typically, attackers would aim to first take over the account of a domain user (like John or Frank) via a phishing campaign. Next, they would use PowerShell scripts, such as PowerSploit, PowerShell Empire, or native PowerShell commands, to enumerate users and admins on that computer. They would then list the local admins and admins with higher privileges accessible from the compromised computer.
For Security teams, detecting a recon attack of this type is difficult because common Windows events are being triggered, and investigating each such event is labor-intensive and time-consuming.
What Is an AD Attack Path?
Using various techniques, the attackers would then move from one computer to the next, or one compromised user account to the next and escalate privileges along the way. Attack paths followed by an attacker are typically based on least resistance and maximum benefit to the attackers. This approach is aimed at ensuring that the attackers reach their objective with the least number of hops and with the smallest chance of detection.
For example, from Figure 1, the attackers are likely to exploit Frank’s account, a member of the Helpdesk group. That way, they can gain membership to the IT Admins group via Frank’s account. Also, the IT Admin group is a member of the Domain Admin group. So, Frank’s account would give the attackers more privileges to advance their attack.
A path that attackers can take on their way to reach a “crown jewel asset,” such as a Domain Admin account or Domain Controller, is called an AD attack path. As described in the example above, this path can consist of nearly any combination of user and administrator accounts, computers, groups, and other Active Directory objects.
Identifying all attack paths and prioritizing them for mitigation is an important first step of Microsoft Active Directory security assessment.
What Is Kerberoasting? How Is it Used to Attack Active Directory?
Figure 2 shows a simplified version of Active Directory attack paths that originate from one account and lead to the Domain Controller.
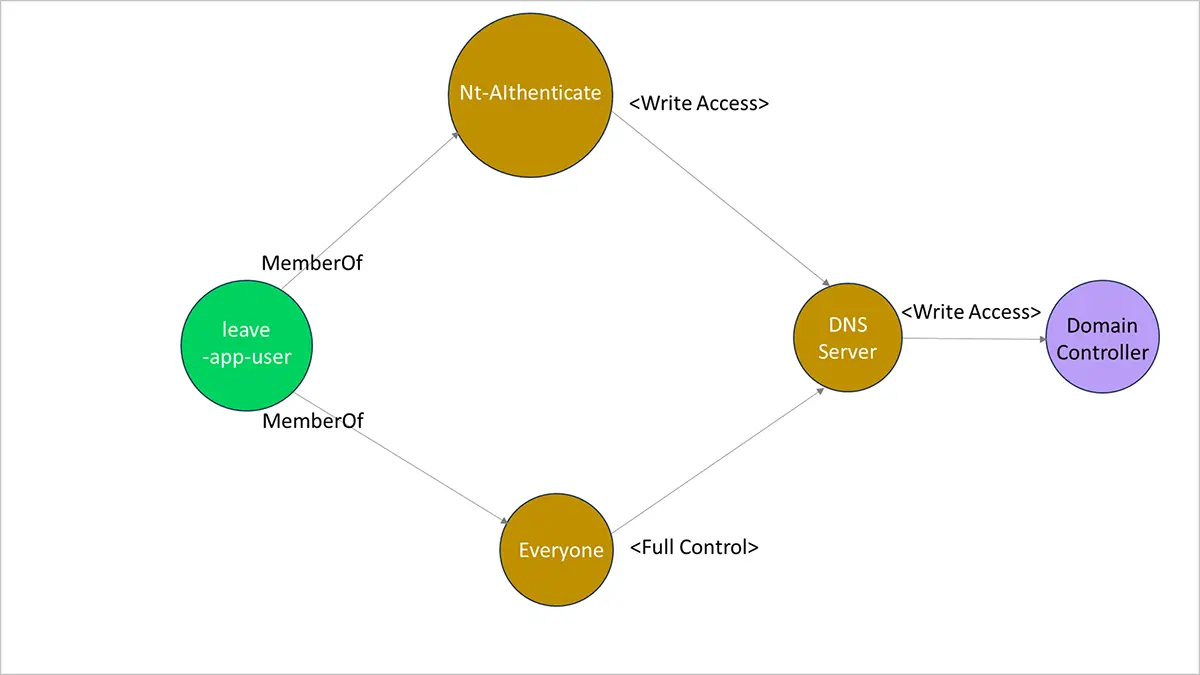
The attackers use a Kerberoastable account in this example. A Kerberoasting attack involves employing tools, such as PowerSploit, JohnTheRipper, or hashcat, to crack the password of a Kerberoastable service account through offline means. This form of Active Directory attack provides a way for attackers to get higher privileges and maintain persistence in the enterprise. This attack is difficult to detect because detection primarily relies on monitoring abnormal service ticket requests in the event logs. Such abnormal tickets are typically extremely common, and basing alerts on them would result in many false positives.
In the example shown in Figure 2, the attackers take over the leave-app-user account via a Kerberoasting attack and then laterally moves to take over the Domain Controller. So, the attack path can be:
leave-app-user > Everyone > DNS Server > Domain Controller
Or, the attack path can be:
leave-app-user > Nt-Authenticate > DNS Server > Domain Controller
A typical enterprise may have thousands of Active Directory attack paths that could lead attackers to the Domain Controllers. Attackers assess and use attack paths based on various factors, such as the shortest number of hops to the Domain Controller, the most vulnerable set of objects along the path, and so on.
A wide attack surface leads to more potential attack paths, creating a bigger challenge for the Security teams trying to protect and secure Active Directory. Comprehensive Microsoft Active Directory security assessment includes identifying attack paths and taking measures to mitigate the risk posed by these attack paths.
In the next blog, we’ll see how an enterprise can use Acalvio ShadowPlex to detect, respond to, and foil attacks against Active Directory.
COMMENT: In the preceding paragraph, please embed the link in the text “next blog.”
Frequently Asked Questions About Microsoft Active Directory Security Assessment
Active Directory is used to manage a multitude of objects, such as accounts, devices, groups, and applications. The relationships between these objects create paths that can be used to traverse from one object to another. These Active Directory attack paths can be used by attackers to reach nearly any target in the network.
Identifying AD attack paths is one of the first steps that the Security team must take toward securing the network. Identifying AD attack paths is also known as gaining Attack Path visibility.
Microsoft Active Directory enables access to on-premises resources in the enterprise network. Microsoft Azure Active Directory enables access to cloud-based resources, such as Microsoft 365, Microsoft Azure services, and numerous other SaaS-based services.
Just like there are AD attack paths that enable attackers to reach on-premises targets in the network, there are Microsoft Azure AD attack paths that enable attackers to reach cloud-based targets in the network.
AD and Azure AD are prime targets for attackers in the on-premises and cloud segments of the network. Therefore, it’s important for Security teams to gain visibility into attack paths stemming from both AD and Azure AD.
After attackers gain access into the enterprise network, they can query Active Directory from any domain-joined computer. In addition, there are standard Red Team tools for visualizing attack paths from data obtained from Active Directory.
When assessing all available attack paths, attackers would choose the path that is shortest and offers the “least resistance” to reach their target. Typically, attack paths that allow attackers to pivot from object to object with the lowest risk of detection are more likely to be used.
Skilled attackers employ “living off the land” techniques while traversing an attack path. This further lowers the chances of detection.
There are various factors that complicate the task of protecting Microsoft Active Directory. Here are some examples:
- An enterprise often runs network resources such as critical applications, non-Windows Servers, and systems configured via older versions of Active Directory. This makes it difficult to upgrade an existing Active Directory deployment.
- An enterprise may have gaps in their patch management systems and processes. Some systems may get patched sporadically. Patching that is incomplete or ends in an error may not be reviewed and rectified.
- The Active Directory attack surface and attack paths are not fully visible to Security teams. This is a critical weakness in AD security.
Kerberoasting is an attack technique in which an attacker uses any valid domain account to request a Kerberos service ticket for a service and then obtains the password from the ticket by using offline password-cracking methods.
The use of domain accounts to request Kerberos service tickets is part of everyday business activity seen in the network. There is nothing unusual about this activity that causes it to stand out and be noticed by traditional security solutions. This makes it difficult to detect a Kerberoasting attack.
A ransomware attack encrypts data files on endpoints in a network and attempts to exfiltrate data from the network. Ransomware attacks are characterized by the speed with which endpoints on the network are infected. To a ransomware actor, knowledge of attack paths is an important factor in propagating an attack. The more the attack paths that the attacker can leverage, the faster the speed at which ransomware propagates through the network.
Effectively protecting Microsoft Active Directory starts with gaining full visibility into the Active Directory attack surface and attack paths. The Security team can use Acalvio ShadowPlex to see all attack paths that exist in the network. They can use this visibility to take measures required to mitigate the attack surface and attack paths.
Deception Technology powered by Acalvio ShadowPlex offers Security teams the means to effectively detect and respond to attacks against Active Directory attacks. ShadowPlex offers a rich palette of deceptions that look just like targets in Active Directory. When attackers try to interact with these deceptions, high-fidelity alerts are generated and preconfigured response actions are initiated.

