MITRE ATT&CK Use Cases for Cybersecurity
As discussed in this whitepaper, the MITRE ATT&CK framework is a critical technology resource that can help you systematically evaluate your security measures against the potential threats you may encounter. Understanding the weaknesses in your current cybersecurity posture is a crucial step in protecting your digital assets.
What is the Mitre ATT&CK Framework?
The MITRE ATT&CK framework is a knowledge base of adversary tactics and techniques based on real-world observations of cyber attacks. Developed by the MITRE Corporation, it stands for Adversarial Tactics, Techniques, and Common Knowledge. The framework provides a structured and comprehensive way to understand the tactics adversaries use to compromise systems, evade detection, and achieve their objectives. It categorizes these tactics and techniques across various stages of the cyber kill chain, helping organizations better understand and defend against cyber threats.
Let’s explore some important use cases below.
Important Mitre ATT&CK Use Cases
Here is a list of important use cases where the MITRE ATT&CK Framework helps cybersecurity.
1. Cyber Threat Intelligence Application
In today’s rapidly evolving threat landscape, cyber defenders are constantly inundated with threat intelligence data. MITRE ATT&CK offers a crucial use case for cyber defenders, enabling them to effectively integrate and prioritize threat intelligence data. Instead of being overwhelmed by the flood of threat intelligence, MITRE ATT&CK allows defenders to strategically map potential attacker tactics and techniques to the risks identified in threat intelligence data.
This approach allows cyber defenders to move beyond the reactive mode of responding to high-priority alerts and incidents and take a more strategic view of their cyber-defense environment.
2. Red Team Penetration Testing
MITRE ATT&CK is a widely used tool that provides a standard language and taxonomy for red team penetration testing. This tool has become popular in the cybersecurity industry due to its ability to bring a well-organized approach to selecting techniques that red teams can use consistently and in a highly repeatable way.
One of the primary benefits of using MITRE ATT&CK is that it models real-world attackers, making it an ideal tool for red teams to build detailed and accurate penetration plans.
3. Blue Team & SOC Team Use Case
In addition to its usefulness for red teams, MITRE ATT&CK can provide valuable benefits for blue and security operations center teams. By enabling blue teams to quickly and accurately assess ongoing attacks and categorize the symptoms they observe into technique categories, The MITRE ATT&CK Framework can help to identify the attacker and stop the attack chain before it can reach its objectives.
It is important to remember that attacks take time, and it is not always necessary to stop them initially. However, it is crucial to stop them before they can exfiltrate data or cause damage to operations. With MITRE ATT&CK, organizations can gain an advantage in determining the best counter-moves in real-time, even during an ongoing attack.
4. Vendor Assessment
Another important use case for the MITRE ATT&CK Framework is in the area of vendor assessment. By enabling organizations to more carefully and logically assess their current vendors and security controls, MITRE ATT&CK allows for informed decisions before new security controls are implemented. It is important to recognize that not all firewalls or endpoint detection and response (EDR) security controls are the same.
5. Breach & Attack Simulation (BAS)
Another valuable MITRE ATT&CK use case is breach and attack simulation (BAS). BAS is an emerging market focusing on software platforms that automate and operationalize the MITRE ATT&CK framework. Organizations can regularly test their production environments with emulated attacks by automating the framework to identify real-time vulnerabilities.
6. Deployment of Behavioral Analytics
Malware signatures and traditional indicators of compromise (IoCs) are becoming less effective as cyber threat actors can easily modify malware and tools that can make IoCs ineffective. Using behavioral analytics to identify attacker behavior is a more reliable approach.
MITRE ATT&CK Techniques describe how attacks can be achieved without specifying a particular tool, allowing defenders to identify attacks and potentially attribute them based on the list of known threat actors using that technique.
7. SOC Maturity Assessment
Detecting and responding to cyberattacks is the security operations center’s (SOC) responsibility. Vulnerability to attacks can occur if the SOC cannot detect or respond to a certain type of attack. The MITRE ATT&CK Framework provides an important role here by helping to measure SOC’s maturity and effectiveness. Testing the techniques within the framework enables organizations to assess the effectiveness of their SOC and defenses against likely cyber threats.
8. Prioritization of Threat Detection
Another important MITRE ATT&CK use case is threat detection prioritization. Often even well-resourced teams cannot defend against all attack vectors. The MITRE ATT&CK Framework can help teams prioritize their threat detection efforts by providing a blueprint. Teams may prioritize certain detections that identify the unique techniques used by a specific attacker group or focus on threats that occur earlier in the attack lifecycle.
9. Attacker Group Tracking
To track relevant behaviors of adversary groups in their sector or vertical, organizations frequently concentrate their monitoring efforts on known behaviors. The ATT&CK framework evolves continuously to align with emerging and evolving threats. As a source of truth, the framework helps organizations understand and monitor the behavior and techniques used by hacker groups.
10. Adversary Emulation
During a penetration test, the organization’s resiliency against realistic cyber threats is tested. Simulating the operations of specific threat actors can be helpful, and having defenses in place against commonly-used tactics is vital.
MITRE ATT&CK can assist in verifying the adequacy of an organization’s defenses against real-world threats. It provides information about potential attack vectors and the adversaries known to use them.
11. Assessment of Defensive Gap
To identify potential vulnerabilities in an organization’s cyber defenses that an attacker could exploit, a defensive gap assessment is conducted. Such gaps can be challenging to discover because they involve searching for what is not present.
The MITRE ATT&CK Framework provides a comprehensive listing of techniques used by attackers at each stage of a cyberattack. This framework can be used to conduct a defensive gap assessment by evaluating whether an organization has adequate defenses in place to detect and prevent each potential attack vector.
What Are the MITRE ATT&CK Matrices?
MITRE ATT&CK Matrices are a visualization representation of the MITRE ATT&CK framework. Each of these organizes information about cyber threats into a matrix format, with columns representing different tactics that adversaries use, and rows representing various techniques associated with each tactic. Each cell in the matrix corresponds to a specific technique within a tactic, providing a comprehensive view of the tactics and techniques employed by adversaries during cyber attacks.
The Matrices are organized under 3 broad categories:
- Enterprise
Covers all the common attack tactics and techniques related to Enterprise attacks. These are further categorized into sub-categories such as Windows, Linux, Cloud. - Mobile
Covers the techniques and tactics seen in cyber attacks involving device access and associated network effects. The matrix covers the Android and iOS platforms. - Industrial Control Systems (ICS)
This covers the tactics and techniques seen in attacks on industrial control systems.
The following image shows a sample Matrix:
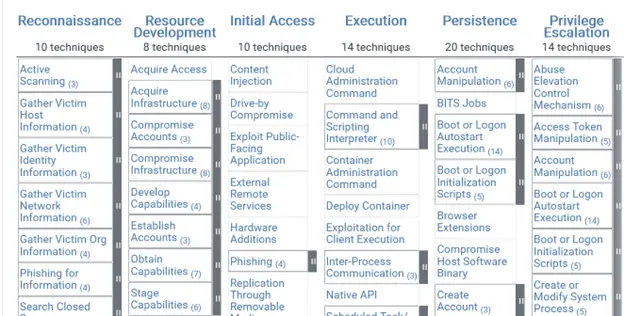
All the latest Matrices are available on the MITRE website.
MITRE ATT&CK Containers Matrix
The MITRE ATT&CK Containers Matrix is an extension of the MITRE ATT&CK framework specifically focused on techniques and tactics used in attacks on containerized environments, such as Docker and Kubernetes. These containers are used to deploy and manage applications. The MITRE ATT&CK Containers Matrix provides a structured and comprehensive overview of the tactics and techniques that are seen in attacks on these environments.
MITRE ATT&CK vs Cyber Kill Chain
The MITRE ATT&CK Framework and the Cyber Kill Chain are both cybersecurity-related models used to understand and respond to cyber threats.
The MITRE ATT&CK Framework was created by the MITRE corporation, it lists the tactics and techniques that adversaries use during cyber attacks. It provides a detailed mapping of these tactics and techniques, organized into a matrix format. The Cyber Kill Chain, developed by Lockheed Martin, focuses on the stages of a cyber attack from the perspective of the attacker.
Security professionals use the MITRE ATT&CK Framework to analyze and understand real-world adversary behavior, assess their own defenses against known tactics and techniques, and improve their overall cybersecurity posture. The Cyber Kill Chain is often used by security teams to visualize and understand the progression of an attack, identify potential points of intervention or detection at each stage, and develop strategies to disrupt or mitigate attacks in progress.
They can be complementary tools used together to provide a comprehensive understanding of cyber threats and how to defend against them.
Mapping Acalvio ShadowPlex Precisely to the Various Attacker Techniques in MITRE ATT&CK
Acalvio ShadowPlex is specifically designed to detect advanced attackers and their tactics, techniques, and tools with absolute certainty. When mapped to the attacker techniques in the MITRE ATT&CK Framework, deception technology disrupts attack chains and provides virtually flawless detection, even for reconnaissance attempts. The chances of attackers evading deception technology are slim, as they will likely encounter it at every turn.
With Acalvio ShadowPlex, enterprises are equipped with optimized and well-architected deception technology to protect against sophisticated threats. By leveraging MITRE ATT&CK, you can more logically organize your efforts and better understand how deception technology can enhance cyber defense resiliency.
ShadowPlex provides the entire spectrum of defensive tactics and techniques listed in MITRE Shield covered by deception. Acalvio is also a Benefactor of MITRE EngageTM.
Frequently Asked Questions
The MITRE ATT&CK framework is a knowledge base of adversary tactics and techniques based on real-world observations of cyber attacks. The framework provides a structured and comprehensive way to understand the tactics adversaries use to compromise systems, evade detection, and achieve their objectives. It categorizes these tactics and techniques across various stages of the cyber kill chain, helping organizations better understand and defend against cyber threats.
Since the MITRE ATT&CK framework is a curated knowledge base for adversary behavior, SOC analysts can use it as a guide for developing, organizing, and using a threat-informed defensive strategy and conducting investigations.
The MITRE ATT&CK (adversarial tactics & techniques) framework is crucial for organizations facing the growing threat of cyber attacks. It offers a comprehensive cyber security framework that allows organizations to understand, prioritize, and mitigate the risks of cyber attacks, providing valuable guidance on preventing and responding to such threats.
Since threat intelligence is the data collected and analyzed to understand adversary motives, tactics, and techniques, MITRE ATT&CK may be considered as threat intelligence, as it also contains information about tactics and techniques threat actors use to target businesses.
The framework is complex and may require specialized expertise to fully utilize its features, especially when it comes to the attribution of threat actors. Also, it focuses heavily on the tools and techniques attackers use but may not provide enough guidance on improving overall security posture and best practices for proactive defense.
The MITRE ATT&CK framework is a repository of tactics and techniques used to help organizations better understand their risk posture and identify gaps in their security controls that attackers may exploit.
It is created to assist threat hunters, defenders, and red teams in categorizing cyber attacks, attributing them to specific threat actors, identifying their objectives, and evaluating an organization’s risk posture.
MITRE ATT&CK is a threat modeling framework for understanding and categorizing adversaries’ tactics, techniques, and procedures (TTPs) in cyber attacks. It can be used to build a comprehensive threat model by identifying potential threat actors and their methods.
The MITRE Corporation developed the MITRE ATT&CK Framework. MITRE is a not-for-profit organization that operates federally funded research and development centers (FFRDCs) to research solutions in areas such as cybersecurity, defense, and healthcare.
MITRE updates and publishes the ATT&CK Framework to reflect emerging threats, new techniques observed in real-world cyber attacks, and feedback from the cybersecurity community. They collaborate with industry partners, government agencies, and cybersecurity experts to update the framework.
By providing a structured and systematic approach to understanding, detecting, and mitigating ransomware attacks, the MITRE ATT&CK Framework helps organizations assess their current security posture and identify gaps in defenses. By studying the standard techniques used by ransomware attackers, organizations can better anticipate and mitigate potential attacks. By mapping ransomware techniques to the MITRE ATT&CK framework, organizations can develop more effective detection and response strategies. This includes implementing security controls and monitoring systems to detect early signs of ransomware activity.

