FrostyGoop: Defending Against ICS Protocol Exploits
The Cyber Security Situation Center (CSSC) in Ukraine highlighted a new industrial control systems (ICS) specific malware known as FrostyGoop in April 2024. This malware was used in cyber attacks that impacted a municipal district energy company. This company provided central heating to over 600 apartment buildings. Remediation of the incident took over two days, leaving civilians exposed to sub-zero temperatures.
What are the implications of ICS protocol-specific malware?
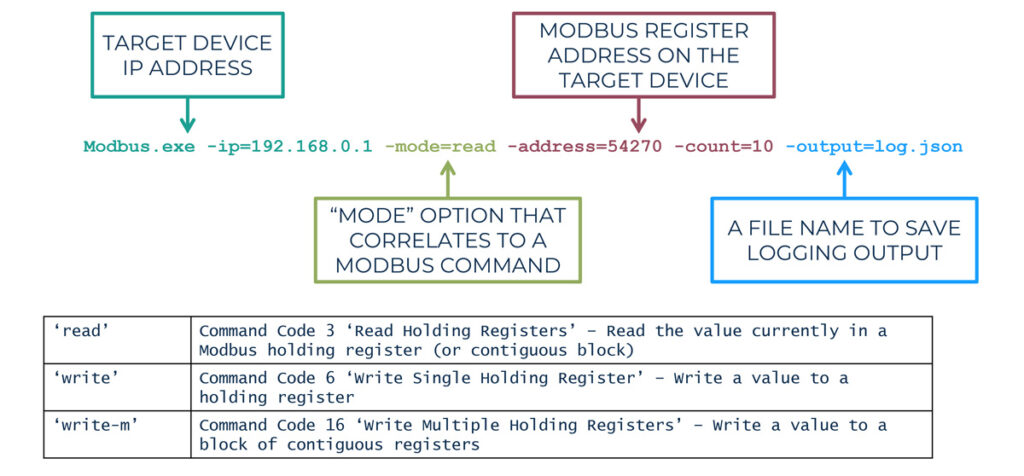
Malware has traditionally been focused on IT infrastructure. OT assets have unique characteristics and protocols, with ICS-specific protocols being used for administration and monitoring. Modbus is a popular ICS protocol, extensively used in OT assets such as Programmable Logic Controller (PLCs).
FrostyGoop malware has the ability to send specific opcodes over Modbus to set register values that can control the operation of a PLC. In this exploit sequence, attackers were able to send remote protocol commands resulting in PLC operations to be disabled.
Why are remote protocol exploits challenging in OT/ICS?
Modern IT protocols, such as HTTPS/TLS have security built into the protocol, providing protection against unauthorized clients attempting remote protocol exploits.
Many of the ICS protocols were defined prior to the work on incorporating security into the protocol itself. As a result, several of the popular ICS protocols, including Modbus, BACnet do not have support for security built into the protocol.
The ICS protocols are unauthenticated and do not support encryption, enabling a wide variety of protocol specific exploits. These range from unauthorized clients attempting remote protocol exploits to man-in-the-middle attacks, protocol replay attacks.
The exploitable attack surface combined with the mission critical nature of OT assets makes protocol exploits an important threat vector. The rise of real-world malware that exploits weaknesses in these protocols is increasing the importance of strengthening OT security.
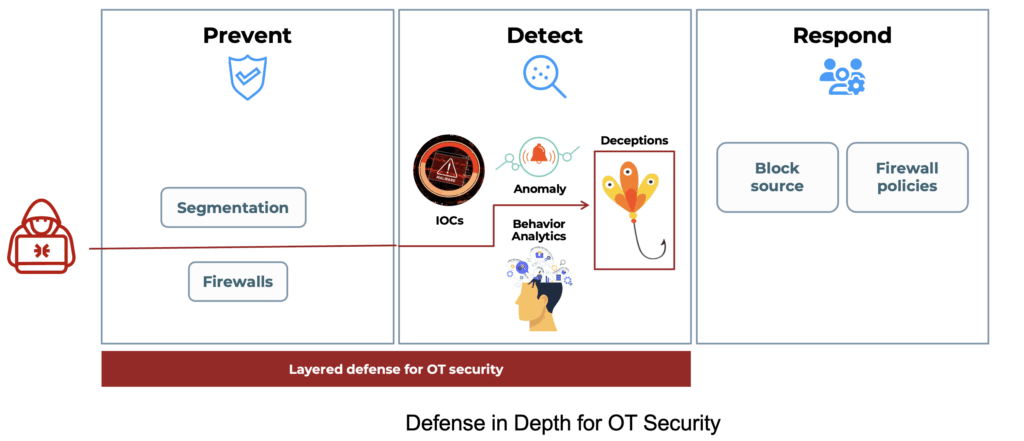
Defender’s perspective: moving beyond segmentation to threat detection
OT security has traditionally relied on network segmentation and air gapping to isolate the assets and reduce the risk of exploits. Segmentation is a necessary prevention-based security control and is essential for reducing the attack surface in OT.
The advent of malware that exploits ICS specific protocol weaknesses is increasing the need for OT security to adopt an “assume compromise” security posture. There are multiple avenues to bypass segmentation and prevention controls, ranging from exploits targeting internet facing OT assets (this was the exploit vector in the Ukraine attack) to insider risk from OT plant administrators and contract staff.
A layered defense approach that combines prevention with threat detection is essential to combat ICS protocol specific exploits.
Threat detection strategies for OT security
OT assets have unique characteristics that require a tailored approach for threat detection. OT assets are often incompatible with agent-based security controls, making endpoint-centric detection (such as EDR) less applicable. Log analytics is also less effective, with the availability of logs and the variation of log formats resulting in challenges for OT security.
OT security has relied on network-centric threat detection, based on Network Detection and Response (NDR) that involves an analysis of the network traffic to find known malicious traffic patterns and also identify anomalous patterns that can identify potential malicious activity.
ICS protocol specific malware, such as FrostyGoop, is challenging to detect with the malware having precise awareness of ICS protocols, such as specific values and opcodes in the Modbus protocol. This level of precision implies that anomaly-based approaches are less likely to identify and flag these exploits. Anomaly-based detection is commonly deployed at the core switch in an OT environment, removing visibility for threats that target assets connected to leaf switches (such as unauthorized commands sent to PLC devices).
Defenders looking to gain visibility for ICS protocol specific exploits are deploying decoys that represent traps for the attacker. Decoys representing OT specific assets have the ability to identify ICS protocol exploits without requiring baselining/tuning and detects threats targeting assets connected to leaf switches as well, in addition to assets connected to the core switch.
Attacker’s perspective: OT deception for threat detection and threat hunting
Consider an OT environment, such as an energy provider, that follows the deployment architecture in the Purdue OT reference architecture. OT security teams deploy PLC decoys that have support for ICS protocols, such as Modbus and BACnet.
The attacker gains access to the OT environment and brings in FrostyGoop as ICS specific malware.
The attacker performs reconnaissance to identify exploitable PLCs prior to the use of FrostyGoop that targets individual targets with Modbus protocol exploits.
Sample attacker command sequence:
- Reconnaissance to find target PLCs that support Modbus protocol:
nmap <subnet CIDR> -p 502
- Protocol specific exploits to disable/shutdown device:
<Execute FrostyGoop on target devices>
By introducing decoys in the environment, the attacker finds decoy devices being surfaced in step a above. OT security teams get notified of this activity, enabling response actions prior to the execution of step b.
This early warning system combined with the high-fidelity of alerting enable defense teams to take rapid response actions to isolate the threat and protect the assets.
Acalvio is the leader in autonomous cyber deception, defending against APTs, insider threats, identity threats, and ransomware. Its AI-powered Preemptive Cybersecurity Platform delivers threat detection across IT, OT, and cloud.