How ShadowPlex detected an advanced red team attack?
Why Red Teaming Exercises Are Critical to Security Assessments?
Red teaming is a structured simulation of real-world adversary tactics, used by organizations to evaluate their ability to detect, respond to, and contain cyberattacks. These exercises test the maturity of the security program by exposing gaps in prevention, detection, and response.
There are several forms of red teaming. One commonly used method is Capture the Flag (CtF), which presents teams with objectives to compromise specific systems or data while evading detection.
On the defensive side, blue teams are responsible for deploying and managing security controls designed to resist the simulated attacks. These engagements provide critical insight into whether those defenses are actually effective under adversarial pressure.
Mature organizations conduct red teaming on a recurring basis. It helps surface blind spots, validate security control effectiveness, and sharpen the response process—all without the cost of a real breach.
A case of a failed red team exercise
A large enterprise facing constant cyber threats initiated a red team assessment to uncover defensive gaps and test its readiness against a targeted attack.
The objective for the red team was clear: gain control of a domain administrator account within Active Directory (AD).
To achieve this, the red team used a stealth technique—Link Local Multicast Name Resolution (LLMNR) poisoning, a form of Man-in-the-Middle (MITM) attack. Using tools like Responder.py or Inveigh.ps1 they intercepted network traffic to harvest credentials.
With these credentials, they escalated privileges and successfully took control of AD.
What are Man-in-the-middle attacks and why are they difficult to detect?
Man-in-the-Middle (MITM) attacks occur when an adversary positions themselves between a legitimate user and their intended destination to intercept or manipulate traffic.
One widely exploited MITM technique in Windows environments is LLMNR poisoning. LLMNR (Link Local Multicast Name Resolution) serves as a fallback mechanism for hostname resolution when DNS fails. Attackers exploit this fallback by intercepting broadcast traffic, tricking devices into sending credentials to a malicious host.
Because LLMNR operates at the local network level and often lacks strong authentication, it creates a low-friction path for attackers to collect credentials and pivot deeper into the environment.
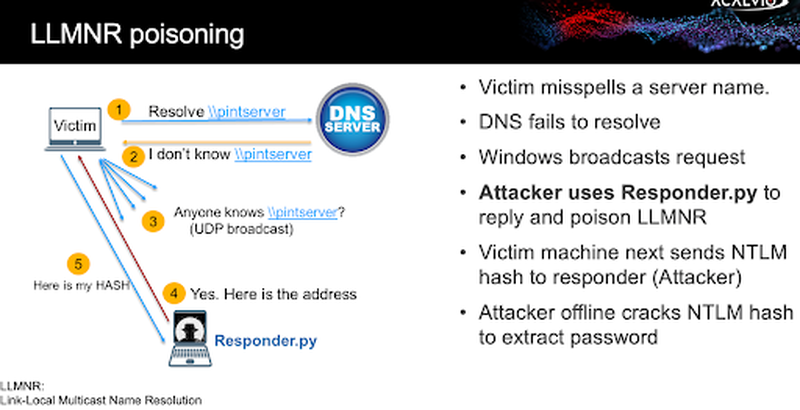
Figure 1: LLMNR poisoning attack
Why LLMNR Poisoning Is Difficult to Detect?
LLMNR poisoning is notoriously hard to detect because the attack typically occurs on an endpoint fully controlled by the attacker. With no endpoint detection and response (EDR) tools in place and logging often disabled, there’s little visibility into the malicious activity taking place.
Red teamers use this technique to quietly capture privileged credentials, which are then used for lateral movement. These can include domain admin credentials—giving them complete control over Active Directory and, by extension, critical systems.
If the red team achieves its objective without triggering any alerts, it’s considered a failure of the defensive side of the exercise. This result exposes real weaknesses in monitoring, visibility, and detection strategy that must be addressed.
How the blue team countered this threat using cyber deception?
Recognizing the blind spot in detecting MITM attacks like LLMNR poisoning, the blue team deployed ShadowPlex to introduce deception-based detection into the environment.
Using ShadowPlex, they generated deceptive LLMNR broadcasts—bait designed to attract adversaries scanning for exploitable name resolution traffic.
When the red team engaged with the decoy broadcast, ShadowPlex triggered an immediate alert, enabling the defenders to detect and respond before further escalation.
This scenario highlights the strategic value of deception: turning attacker behavior into a reliable detection signal and transforming a previously undetectable threat vector into one the defenders could see and act on.
Conclusion
Red teaming exercises are only as valuable as the insights they generate. When stealthy techniques like LLMNR poisoning go undetected, they expose critical weaknesses in defensive coverage. This case demonstrated how traditional controls can miss low-level network attacks that operate beneath the radar of EDR and logging. By introducing deception technology with ShadowPlex, the blue team converted a blind spot into a detection point. Cyber deception does not replace existing defenses; it complements them by surfacing attacker behavior that would otherwise remain invisible. For organizations focused on improving detection fidelity and reducing dwell time, deception offers a practical and proven advantage.
Ready to strengthen your security posture with deception?
Contact us to learn how ShadowPlex can help your team detect advanced threats that other tools miss.

