Beyond patching: why preemptive defense is essential to secure SAP
SAP as a prime target for cyber attacks
SAP is core to an organization’s infrastructure. Enterprises store business-critical data in SAP, including logistics, inventory management, and financial data.
Given the sensitive nature of the data, SAP is a prime target for cyber attacks. The risk of exfiltration and loss of sensitive corporate data makes it essential for cyber defense teams to adopt a robust security strategy to protect SAP.
A recent exploit in September 2025 against a global manufacturer had a widespread impact, forcing the manufacturer to shut down production facilities and causing IT systems to go offline for extended periods.
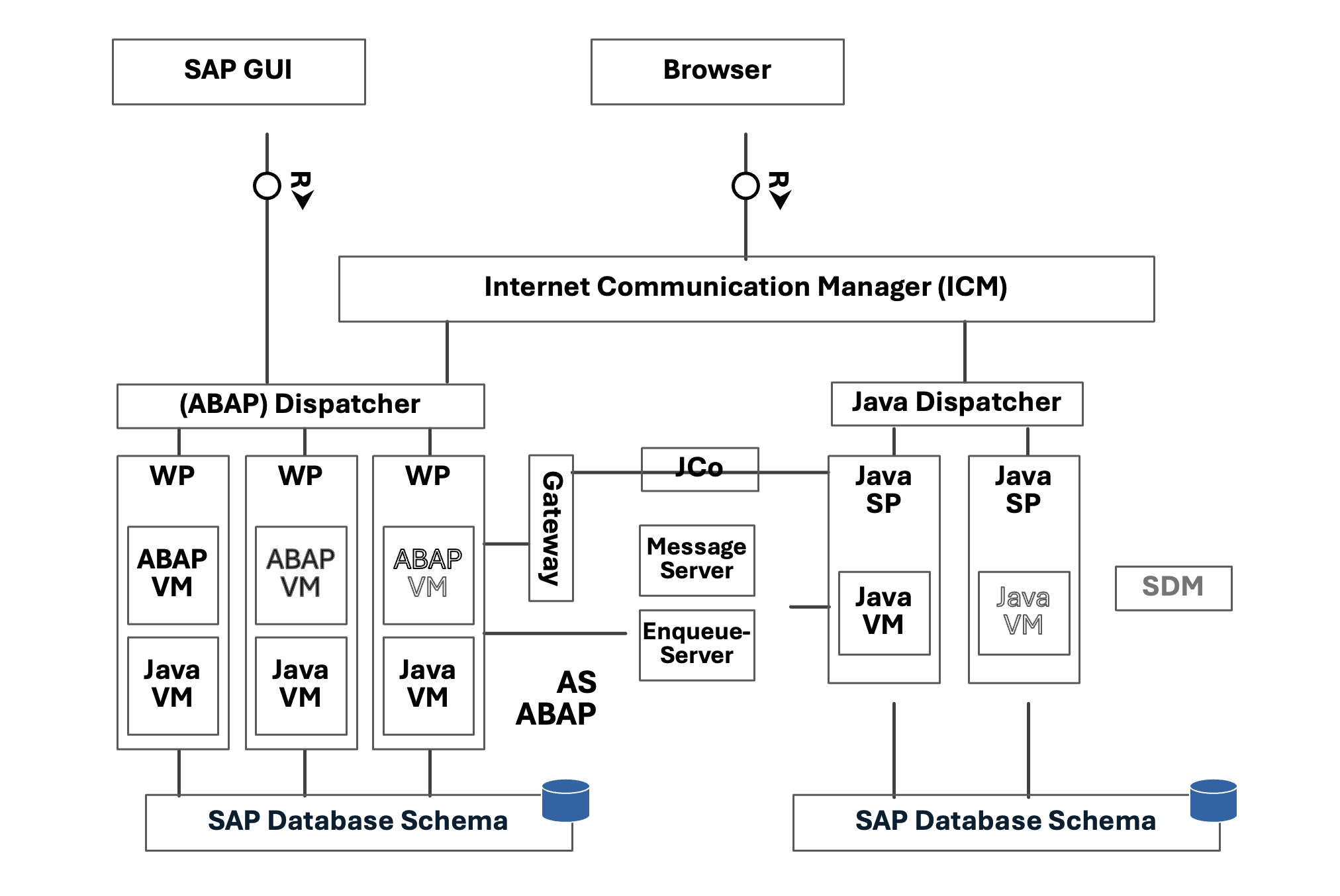
Figure 1: SAP NetWeaver architecture
Threats targeting SAP
SAP is targeted by a variety of threats, including APT threats, ransomware, and insider threats. APT threat groups such as Silk Typhoon (UNC5221) and APT41 have been known to exploit vulnerabilities in SAP products, such as NetWeaver. These exploits target public-facing SAP servers for initial access and look for sensitive data to exfiltrate.
Ransomware groups are actively targeting SAP, with groups such as Scattered LAPSUS$ Hunters being active and exploiting SAP infrastructure for data exfiltration and operational disruption. The widespread deployment footprint of SAP, along with its extensive documentation of the SAP deployment architecture, is resulting in exploits specifically tailored to SAP environments.
The “Scattered LAPSUS$ Hunters” (ShinyHunters) exploited a series of CVEs (for example, CVE-2025-31324 and CVE-2025-42999) to gain access to the SAP infrastructure. Once the attacker gained access to the SAP systems, they pivoted to find and exfiltrate the sensitive data from the data stores. The CVE-2025-31324 had a CVSS score of 10.0, the highest possible severity ranking. This highlights the prevalence and importance of SAP-specific exploits.
Advances in GenAI are significantly increasing the attack surface. Adversaries are leveraging GenAI to convert natural language prompts into offensive tooling.
Why a modern SAP security strategy needs to evolve beyond prevention
Defenders recognize that SAP infrastructure is a prime target. Prevention-based controls for SAP systems primarily focus on patching and network segmentation.
The focus of security teams is primarily on applying patches rapidly for new security fixes. Rapid patch application is an essential security strategy, as it helps reduce the exploitable attack surface.
The patch application process for enterprise-grade products, such as SAP, is challenging for security teams. With an average of 10 to 15 patches and security notes published each month, security teams struggle to ensure systems are properly patched. SAP deployments often involve multiple components; the patch application process is complex to ensure that individual components are correctly patched and the system continues to function without impact.
Network segmentation is also applied in many organizations as a preventive control. Segmentation helps reduce exposure risk and the radius of the exploitable attack surface. While segmentation plays a vital role in reducing the risk of network threats, modern attacks are leveraging identities to gain access to critical assets like SAP and leveraging trusted connection pathways to bypass segmentation restrictions.
“Assume compromise” security posture and threat detection.
Security teams recognize that attackers can gain initial access and perform lateral movement through many pathways within an organization. This is despite good security hygiene around prevention controls.
Assume compromise is widely accepted as a necessary security posture. The organization must assume the adversary will gain initial access. The adversary needs to perform a series of attack steps as part of an attack pathway before they can complete their mission of compromising the SAP infrastructure.
What makes threat detection for SAP infrastructure challenging
Traditional IT infrastructure typically deploys EDR as the primary mechanism for threat detection. This is an endpoint-centric detection.
EDR deployment on SAP systems requires careful consideration and planning. Security agents can affect the performance and functionality of the SAP infrastructure. Organizations might choose not to deploy EDR on SAP systems or perform whitelisting of specific folders and processes.
The limited scope of the EDR rollout results in threat detection gaps on systems that host SAP infrastructure. EDR solution providers have published advisories recommending a phased and controlled rollout of EDR on SAP systems to avoid impacting production workloads.
Log analytics is challenging, with SAP systems having proprietary log formats. As SAP rolls out enhancements to its products (NetWeaver, HANA), log formats can change over time, affecting log analytics. The Scattered LAPSUS$ Hunters exploits did not leave any trace in the SAP application audit logs, with the stealthy attack techniques evading log analytics-based detection measures.
Preemptive security for SAP infrastructure
A strategy anchored around rapid detection of the threat and deflecting the threat away from the target is an effective approach as part of a defense-in-depth approach to SAP security.
This approach, known as preemptive security, involves anticipating threats targeting SAP systems and setting traps for attackers. The traps serve to detect the threat and deflect the attacker away from the high-value assets.
The traps are a combination of decoys (new targets for the attacker deployed in the network) and honeytokens (deceptive credentials and data deployed on real systems).
Consider a SAP NetWeaver deployment where an Oracle database backs the SAP application. Attackers can target the database to gain access to sensitive data stored in it.
An illustrative architecture diagram of an SAP infrastructure environment and the related deception deployment is shown below.
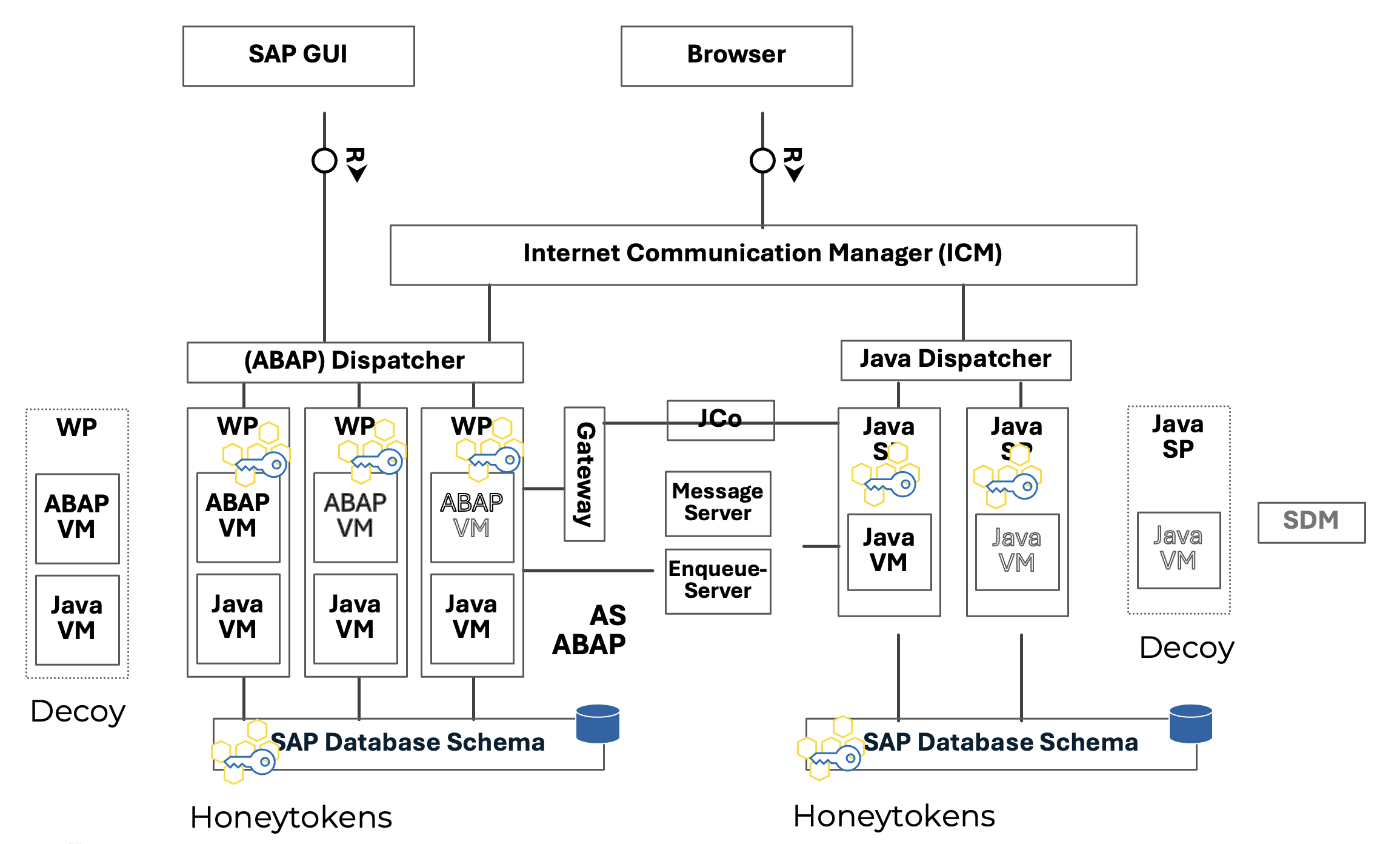
Figure 2: SAP NetWeaver architecture: with deceptions (decoys and honeytokens)
Attack scenario and role of preemptive defense
Consider an attack scenario where the threat actor has an initial foothold in the enterprise. The attacker’s goal is to get access to the sensitive data stored in the SAP database and exfiltrate it. The defense team has placed deceptions (decoys and honeytokens) in the environment (SAP decoys, honeytoken accounts in Active Directory, honeytokens on endpoints).
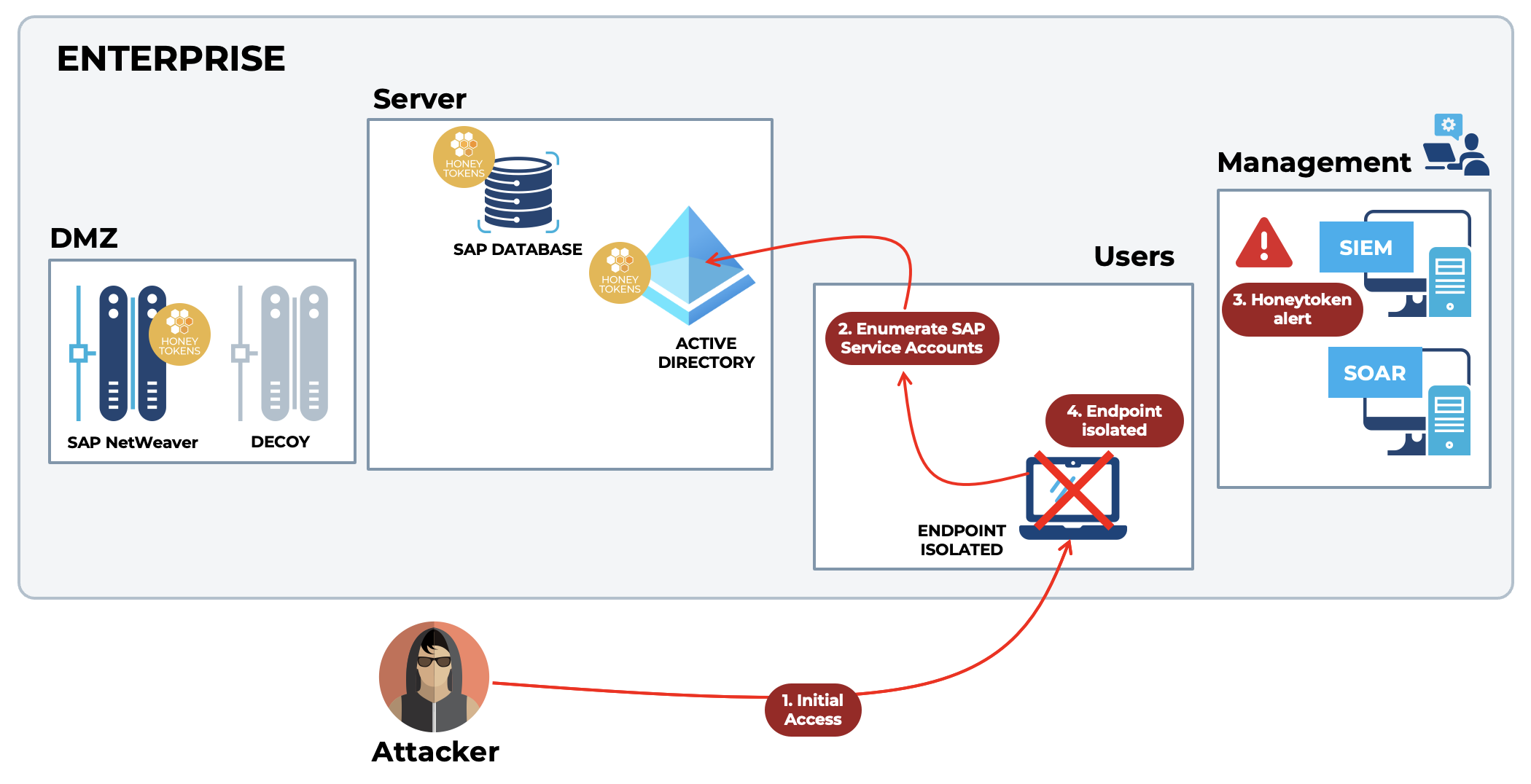
Figure 3: attack scenario with early detection based on preemptive defense
The attack scenario is outlined below. The attack steps are:
- The attacker gains initial access to the environment. An example of this is by phishing an employee to gain a foothold on their laptop.
- The attacker performs enumeration to identify SAP service accounts in Active Directory (AD). The attacker is attempting to exploit the service account to gain access to the SAP database and exfiltrate data.
- The attacker finds such a service account and attempts to use it. This is a honeytoken account, placed in AD and made enticing for the attacker to exploit (for example, a SAP service account with a name that starts with “SAPService,” which makes it look interesting and relevant to the attacker). The usage attempt triggers an immediate alert for SOC teams, which is surfaced in the SIEM/SOAR.
- Response actions (automated based on policies or SOC-initiated) are taken, the endpoint is isolated and the attacker is stopped. This ensures the exploit is stopped and the sensitive data in SAP is protected.
Threat intelligence for initial access exploits
Attackers are gaining initial access by sending specifically crafted exploit sequences to SAP systems. The CVE-2025-31324 involved the threat actor sending specially crafted HTTP requests to the /developmentserver/metadatauploader API endpoint in SAP. Attackers have used this vulnerability to deploy web shells (example helper.jsp and cache.jsp) to achieve persistence and execute offensive commands.
To detect initial access exploits, defenders can deploy internet facing properties that represent SAP NetWeaver and related SAP products. Attackers that attempt known or novel CVE exploits would target these properties, providing a source of generated threat intelligence for defenders.
Threat intelligence teams gain targeted threat intelligence that provides visibility to initial access exploit techniques. The use of novel vulnerabilities, the credentials used, the source IPs and geolocation of the adversary are surfaced as threat intelligence.
Acalvio ShadowPlex: automated and scalable preemptive defense to secure SAP
Preemptive defense is a proven approach for securing high-value assets such as SAP. ShadowPlex provides packaged solutions, known as deception playbooks, that make it easy for the administrator to roll out a focused strategy for securing SAP infrastructure.
ShadowPlex automates the deployment and refresh of honeytokens across the enterprise to detect threats targeting SAP infrastructure. ShadowPlex provides purpose-built decoys that represent SAP assets (such as a SAP database decoy) that are deployed inside the enterprise and public-facing properties (for example, SAP NetWeaver web portal) that are deployed on internet-facing assets. ShadowPlex uses AI to automate the deception strategy, including the deployment of deceptions that are relevant for the enterprise environment and placing the deceptions along attacker pathways.
ShadowPlex captures attacker actions and performs automated triaging to generate actionable alerts and surface targeted threat intelligence for the defense teams.
Summary
SAP infrastructure hosts sensitive data related to financial, supply chain planning, and inventory management. Threat actors such as Scattered LAPSUS$ Hunters are focusing on SAP exploits. SAP security is challenging to operationalize; organizations often struggle to keep pace with the rapid pace of patches. Defense teams have had limited detection coverage for SAP, and SAP systems are usually incompatible with EDR solutions. Preemptive defense based on cyber deception is an effective approach to strengthen SAP security, enabling rapid threat detection and deflecting attacks away from production systems. Adopting this approach safeguards the organization as AI-assisted attacks continue to evolve with novel TTPs being generated on an ongoing basis.
Acalvio ShadowPlex is a robust and proven preemptive cybersecurity platform that strengthens SAP security. This enables organizations to gain immediate benefits and defend against the evolving threat landscape targeting SAP systems.

