Scattered Spider and the Cloud Control Plane: stealthy identity threats
Scattered Spider, also known as UNC3944/Oct Tempest is one of the most active cybercrime groups that has compromised industries across multiple verticals (telecommunications, financial services, healthcare).
The scale and sophistication of this threat actor group is resulting in extensive damage, both in financial losses and loss of intellectual property.
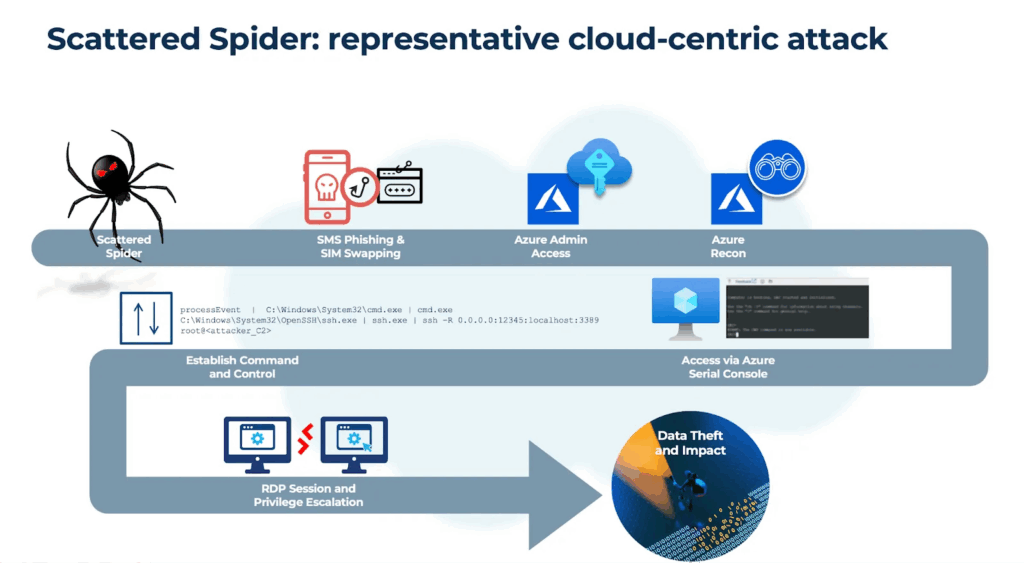
This group has traditionally focused on on premise exploits. Recent exploits have shown an increased emphasis on cloud workloads, especially with identity-driven attacks. This group has been known to target the control plane in the cloud to gain administrative privileges and for lateral movement.
Figure: attack chain for cloud specific exploits performed by Scattered Spider
What is the cloud control plane and why is it a target
The architecture of cloud workloads comprises the control plane and the data plane. The data plane provides the primary function of the cloud service, such as compute instances and storage buckets in the cloud.
The control plane is responsible for management actions and administrative APIs for cloud resources. The cloud control plane is a set of APIs and primitives that allow cloud compute instances, containers, serverless functions to be provisioned/deprovisioned and started/stopped in the cloud.
Attackers, such as Scattered Spider, are targeting the control plane in the cloud as the control plane serves as a central choke point to gain access to cloud resources and data.
While the resources in the data plane vary for each tenant/organization hosted in the cloud, the semantics of the control plane are consistent across cloud tenants. Attackers can create their own tenant in the cloud, disable security controls, fine-tune and perfect an offensive playbook targeted at the control plane, and then repeat this playbook several times to compromise individual tenants/organizations in the cloud.
The consistent semantics and centralized governance makes the control plane a particularly attractive target for cloud attacks.

Figure: Attackers tailor their exploit techniques specifically for the cloud control plane
Scattered Spider and identity exploits targeting the control plane
Control plane exploits are anchored around identity compromise. With identity serving as the fundamental construct for provisioning resources in the cloud, identity compromise is increasingly attractive for attackers that look to elevate permissions and propagate in the cloud. Identity and Access Management (IAM) represents one of the most commonly attacked services in the cloud.
After gaining initial access, Scattered Spider looks to gain administrative access to cloud resources. This involves enumeration of IAM users, including human and non-human (machine identities/service accounts) and looking for cloud credentials (access keys, secrets) to gain access to the corresponding cloud identities.
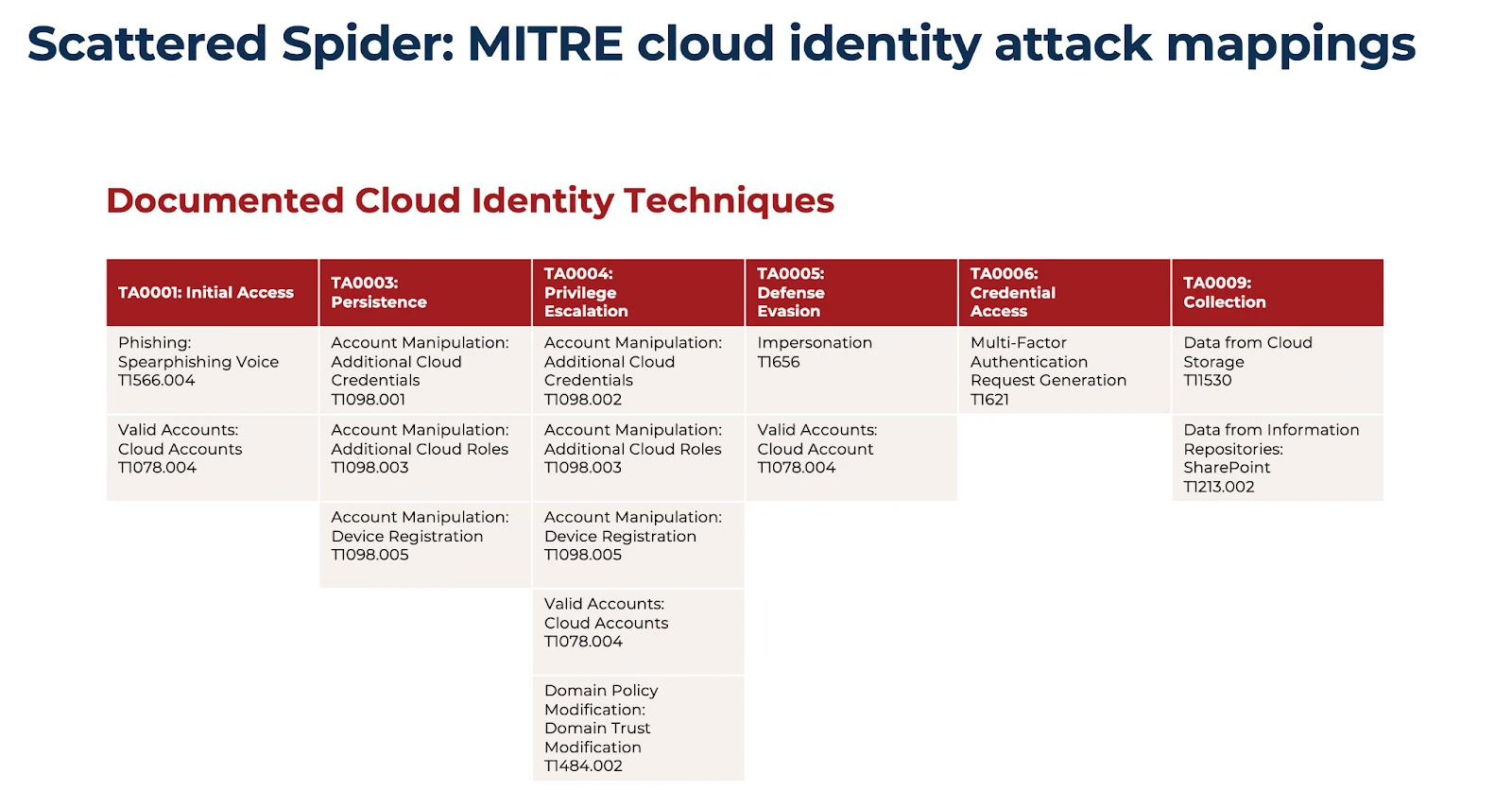
Figure: Scattered Spider and the set of known cloud identity exploit techniques
Defender’s perspective: what makes cloud threat detection challenging
The unique characteristics of cloud workloads makes threat detection challenging in the cloud. Cloud workloads are ephemeral and often short-lived, making it difficult to establish a baseline of “normal” usage in the cloud and identify anomalous usage patterns. This makes anomaly-based detection techniques difficult to establish for cloud workloads.
The volume and variety of log sources makes log analytics difficult for cloud workloads. Defenders have to piece together multiple log sources, with control plane activity being logged in one set of logs (for example, AWS CloudTrail) and data plane activity logged in multiple sources (compute instance logs, storage bucket logs).
While attackers freely pivot across the control and data plane, the disparate set of log sources and the lack of a “session” identifier to tie these actions together makes it difficult for defenders to trace and identify attacker activity through log analytics.
What are cloud honeytokens and what role do they play in cloud security
Honeytokens are deceptive identities and deceptive data in the cloud. Honeytokens represent deceptive identities (human and non-human/machine identities) in cloud IAM stores. Corresponding credentials (access keys, secrets) are deployed across workloads in the cloud.
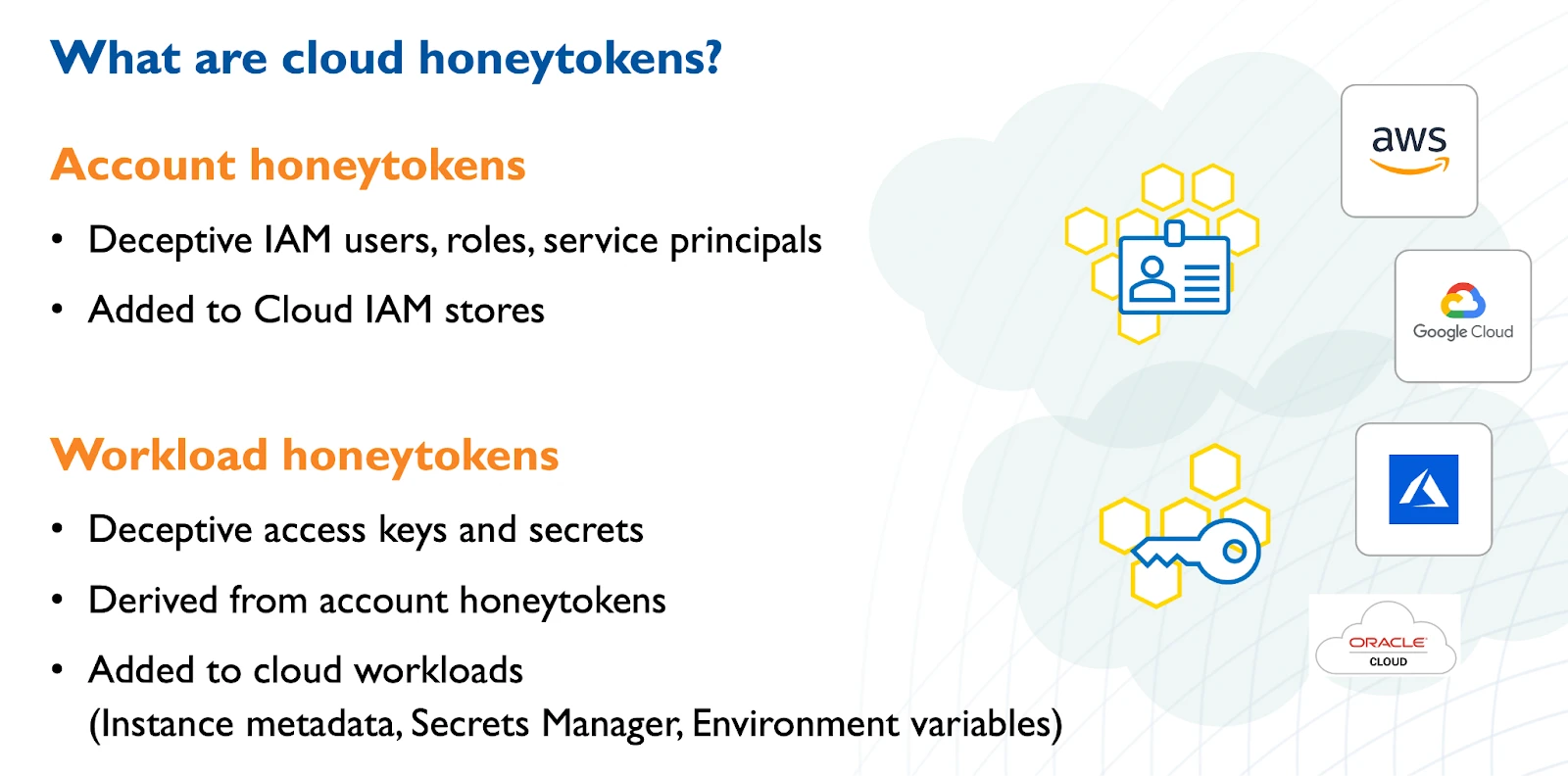
Figure: overview of honeytokens in the cloud
Honeytokens set traps for the attacker as a proactive approach to cloud security. An attacker that looks for privileged identities in the cloud will find the honeytokens, any usage of the honeytokens raises an immediate alert for the Security Operations Center (SOC), stopping the cloud exploit early in the attack lifecycle and protecting the resources.
Honeytokens play an essential role in threat detection and threat hunting in the cloud. This serves as a high-fidelity indicator of cloud threats, safeguarding cloud resources.
Attack scenario: how honeytokens detect cloud identity threats
Let us take an example of an attack targeting identities in the cloud. An attacker gains initial access to the cloud workload, performs enumeration to find privileged identities, and attempts to gain access to the identity (through an “assume role” step in AWS).
Defenders that anticipate these threats set proactive traps in the form of honeytokens that represent IAM admin identities (deceptive IAM Roles). The attacker attempts to assume this role, resulting in an immediate alert for SOC.
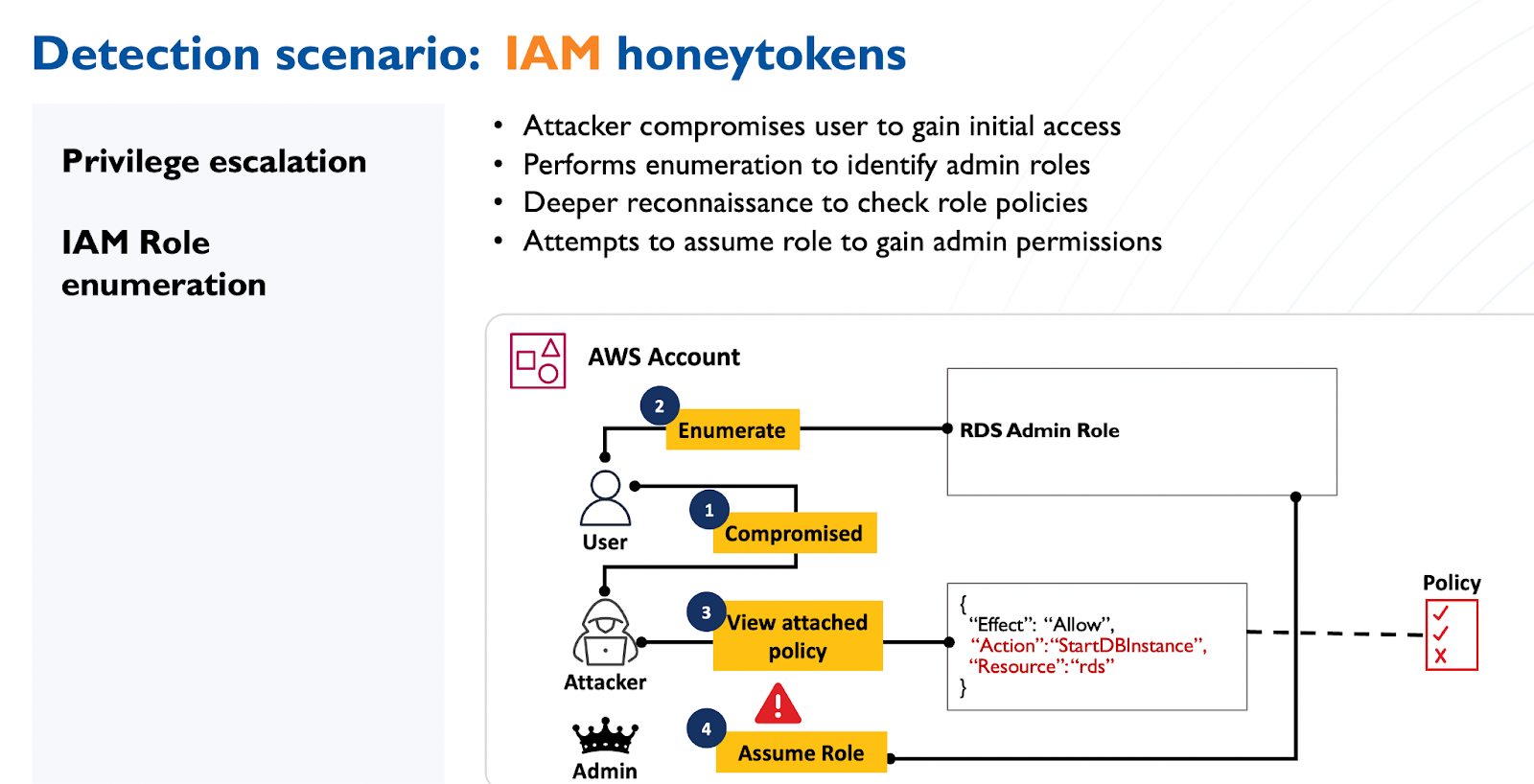
Figure: attack scenario and the role of cloud honeytokens
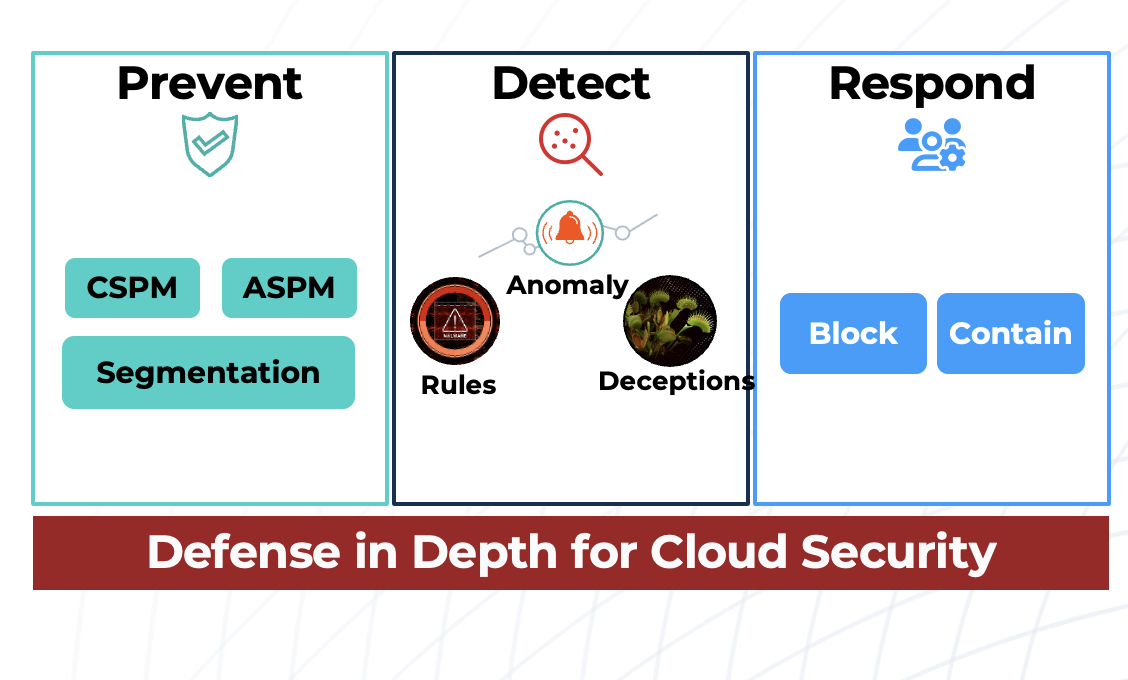
Summary: combating Scattered Spider: defense in depth for cloud security
Advanced threats like Scattered Spider are targeting workloads in the cloud through identity exploits and attacks targeting the cloud control plane. Combating these stealthy threats requires a layered defense approach that combines prevention controls with detection layers that are designed to expand detection coverage.
Prevention controls based on attack surface management approaches reduce the exploitable attack surface. Cloud Security Posture Management (CSPM) solutions provide this pre-attack stage visibility and reduction steps.
A layered detection approach that combines detection for known threats (based on rules) and defenses that can detect evolving threats (based on honeytokens) ensure coverage for a variety of attack techniques in the cloud.
By anchoring cloud security strategy based on proven principles of defense in depth, defenders gain early visibility to a wide variety of cloud threats and protect the cloud workloads.