- Map and close attack vectors to EHRs, imaging archives, and connected medical devices before adversaries exploit them.
- Catch credential misuse early across shared workstations, session tokens, and privileged admin accounts.
- Spot unauthorized access to PHI, billing systems, and provider tools using decoys tailored for healthcare environments.
- Lure evasive threats into decoy apps and cloud workloads to detect ransomware and novel malware

An essential part of a comprehensive security posture
The Health Industry Cybersecurity Practices (HICP) Technical Volume 2, released by the Healthcare and Public Health Sector Coordinating Council, posits cyber deception as an essential part of a comprehensive security posture.
This technical volume guides how Healthcare Delivery Organizations (HDOs) can implement cyber deception techniques like honeypots, honeytokens, and other decoys to strengthen their defense strategy. Several government standards organizations require or recommend active defense and deception, including:
- The 2023 National Defense Authorization Act
- NIST SP 800-172,
- The CISA 2022 – 2026 Strategic Technology Roadmap

Healthcare IT is layered, fragmented, and full of soft spots: Map the attacker’s view.
- Identify shadow admins, unmanaged systems, and stale credentials
- Expose attack paths across hybrid AD, cloud, and legacy EHRs
- Deploy deception to monitor exposed identity and infrastructure assets
- Reduce exposure without relying on scanning or endpoint agents

Credential misuse is how most attacks begin and stealth by undetected.
- Catch misuse of service accounts and session artifacts
- Detect privilege escalation and lateral movement via decoy engagement
- Deploy honeytokens in clinical, administrative, and cloud systems
- Trigger alerts only on real attacker behavior and not anomalies

Collect clear evidence of intent without profiling staff behavior
- Deploy fake patient records, billing files, and admin tools as traps
- Detect attempts to access sensitive data outside approved workflows
- Identify malicious behavior based on interaction, not user baselines
- Capture defensible telemetry to accelerate investigation and containment
When malware adapts faster than signatures, deception makes it visible.
- Detect polymorphic, fileless, and AI-generated malware
- Catch ransomware staging activity before encryption begins
- Lure evasive malware targeting clinical endpoints and portals
- Feed verified alerts into SOC tools for automated response
Strategic Technology Roadmap for Deception Technology and Zero Trust
By overlaying the organization’s computing environment with decoys that lure attackers away from real data, cyber deception not only confuses the attacker but also alerts security teams about every move they make.
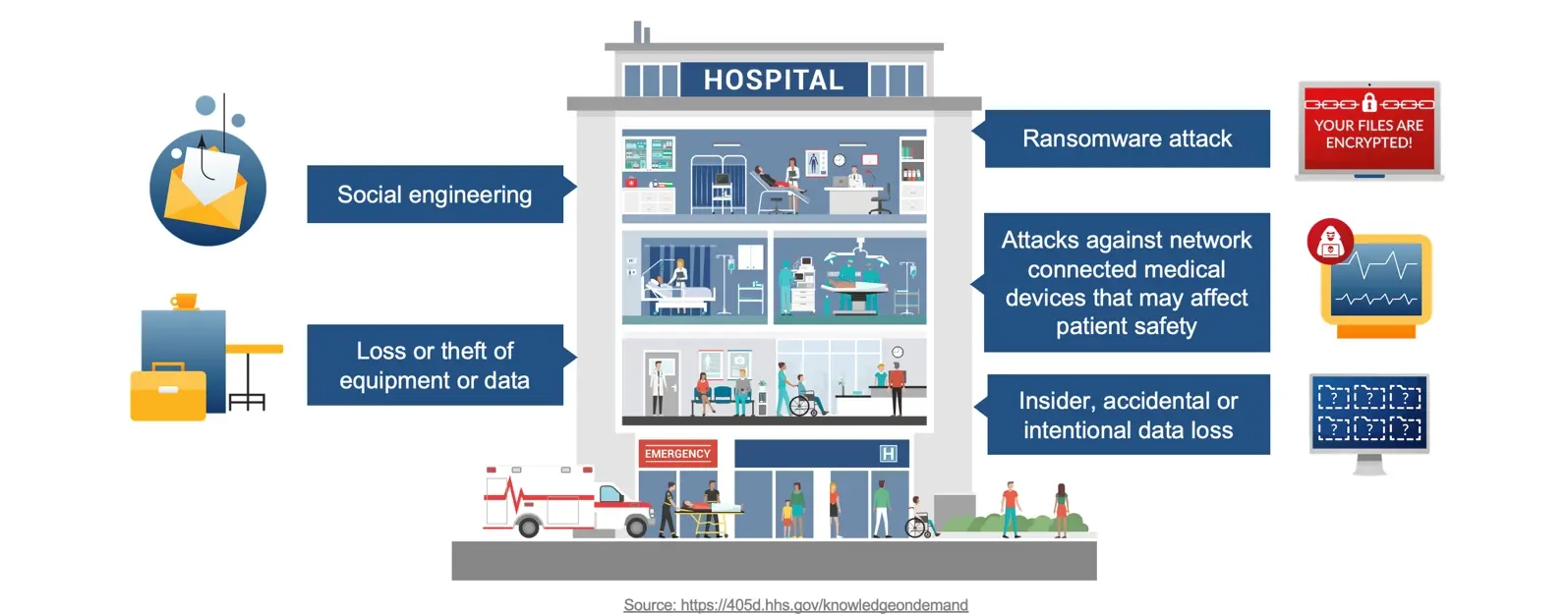
Regardless of size or specialty, Healthcare Delivery Organizations (HDOs) are a prime target for cybercriminals due to their rich trove of sensitive data. Acalvio provides active defense solutions that form the backbone of cyber deception, equipping HDOs with powerful tools to disrupt attacks, provide early warning of intrusions, and minimize the impact of successful attacks.
Frequently Asked Questions
The top cybersecurity threats in healthcare include ransomware attacks, data breaches, and phishing, which compromise critical patient data and disrupt care. Insider threats, vulnerabilities in connected medical devices, and third-party risks further expose healthcare systems to exploitation. To protect sensitive data and ensure operational continuity, healthcare organizations must implement robust cybersecurity strategies.
Cyber deception strengthens healthcare cybersecurity by enabling early threat detection through honeypots and decoy systems, which lure attackers and reduce their dwell time in networks. It enhances threat intelligence by analyzing attacker behavior, improving threat hunting, and providing insights into tactics and vulnerabilities. Deception improves the security posture by adding a layered defense, diverting attackers to decoys, and reducing the attack surface. With faster incident response and cost-effective security measures, it minimizes breaches’ impact, protects patient data, and builds resilience against cyber threats.
Acalvio ShadowPlex is ideal for healthcare organizations due to its visibility, providing unique insights into how attackers view endpoints, reach critical assets, and exploit misconfigurations to reduce the attack surface. It delivers advanced threat detection through realistic deceptions like decoys and breadcrumbs, generating high-fidelity alerts and forensic data when engaged. ShadowPlex enhances investigation capabilities with AI-driven threat hunting and proactive identification of dormant threats, offering a novel approach to understanding adversary behavior. With automated response and seamless integration with existing security tools, it enables real-time threat containment, isolation, and asset protection to safeguard sensitive healthcare systems.
Built for Healthcare Services. Focused on Preemptive Defense
Surface attacker behavior across clinical, admin, and cloud systems: no agents, performance impact, or compliance overhead.
Reduce alert noise and accelerate triage with high-fidelity, intent-based signals that give your team the full picture—no guesswork required.
Protect on-prem and cloud workloads, medical IoT, and third-party systems with deception that adapts to healthcare’s complexity and scale.



