- Create authentic decoys, honeytokens, and credentials that attackers trust.
- Adapt deception dynamically to attacker behavior.
- Detect stealthy credential misuse and privilege escalation paths.
- Disrupt attacker movement inside identity systems.
- Detect stealthy techniques used by APTs and AI-driven attacks early.
- Expose lateral movement and privilege escalation before critical assets access.
- Apply deception across AWS, Azure, and GCP workloads.
- Detect early threats in cloud services, workloads, and identities.
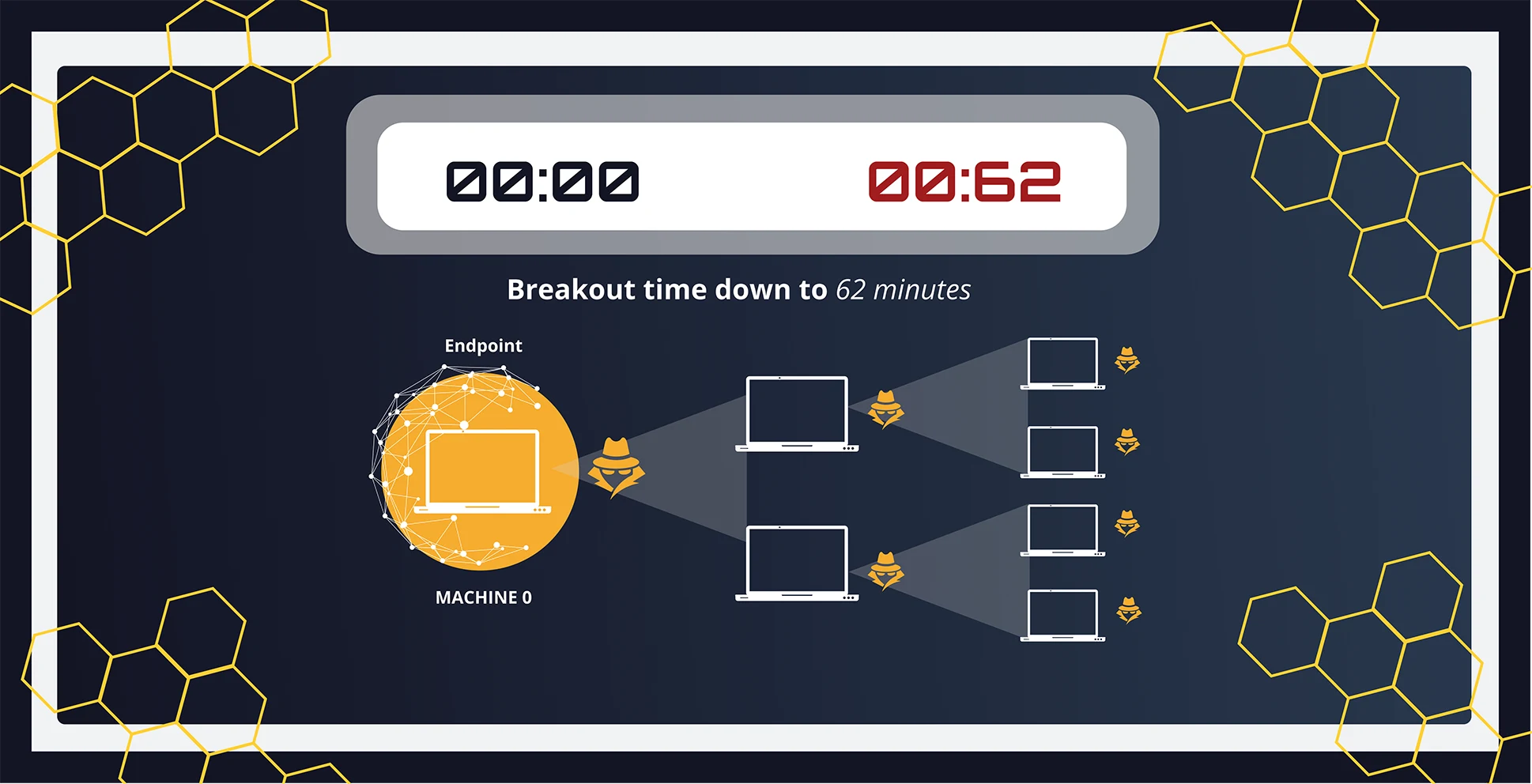
Attackers are fast. Detection must be faster.
- Initial access is quickly followed by recon and credential harvesting
- Privilege escalation and lateral movement happen within minutes.
- Critical systems are targeted long before traditional tools can respond.

- Adversaries escalate quickly using credentials and legitimate tools.
- Traditional detection relies on slow signal emergence and pattern analysis.
- Attackers often breach critical systems before being detected.

- Adversaries blend into legitimate activity to evade early detection.
- Credential misuse and insider-like behavior escape traditional monitoring.
- Deception breaks attacker trust in their tools, slowing operations and exposing intent.

- Exists outside normal workflows—only attacker interaction triggers detection
- Captures intent at reconnaissance and credential harvesting stages
- Detects threats without waiting for pattern recognition or anomaly baselines

- Seed deception assets across endpoints, cloud workloads, identity systems, and OT networks
- Use AI to create realistic credentials, access paths, and services attackers trust
- Adapt deception continuously as environments shift and attacker behavior evolves
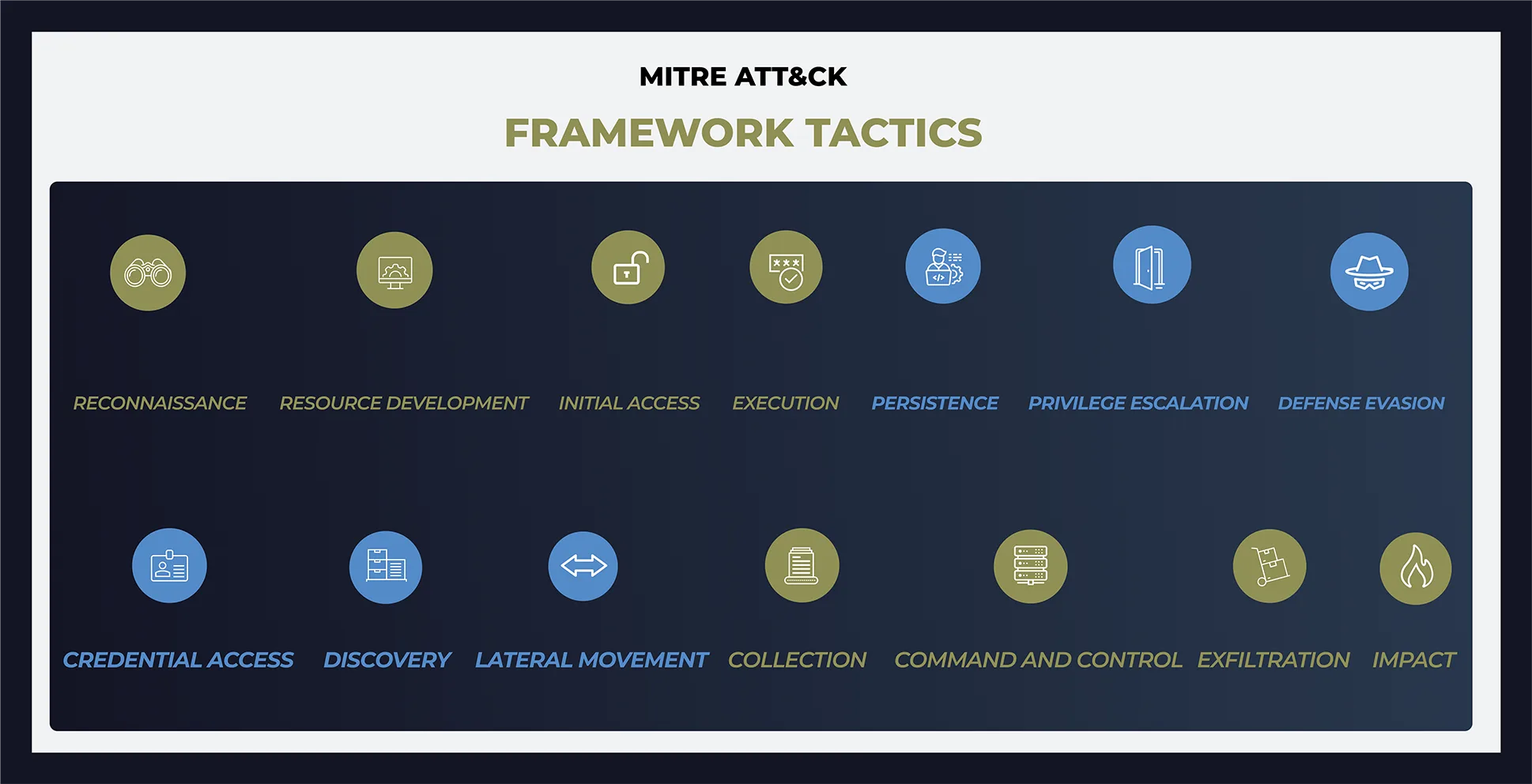
Acalvio aligns with MITRE ATT&CK to expose adversary behavior early in the attack chain.
By planting deception at key stages—reconnaissance, credential access, and lateral movement—defenders gain high-fidelity insights before damage occurs.
Reconnaissance: Deception assets lure attackers during scanning and discovery
- Initial Access: Honeytokens detect use of compromised credentials
- Credential Access: Fake secrets and identity stores expose attacker attempts
- Privilege Escalation & Lateral Movement: Deceptive admin credentials trigger alerts on misuse
Frequently Asked Questions
Adversary breakout time is the duration an attacker takes to move from the initial compromise to broader network access. A shorter breakout time allows attackers to escalate their activities quickly, causing significant damage before detection. Effective defenses focus on minimizing breakout time through continuous monitoring, rapid detection, and network segmentation to limit lateral movement. Reducing breakout time enables faster response and helps mitigate the overall impact of an attack.
Traditional security solutions, like antivirus and firewalls, are often ineffective against new or unknown threats because they rely on known signatures and predefined rules. They struggle to detect modern, dynamic attacks, such as zero-day exploits or advanced persistent threats (APTs), which involve anomalous behavior. To address this, organizations require advanced detection methods like behavioral analysis, machine learning, and real-time threat intelligence for early threat identification and proactive response.
Cyber deception enables early threat detection by deploying decoy systems and data that appear legitimate to attackers. When attackers interact with these decoys, security teams are alerted, enabling early identification of threats. This approach helps organizations detect and respond to attacks before significant damage occurs, enhancing overall security.


