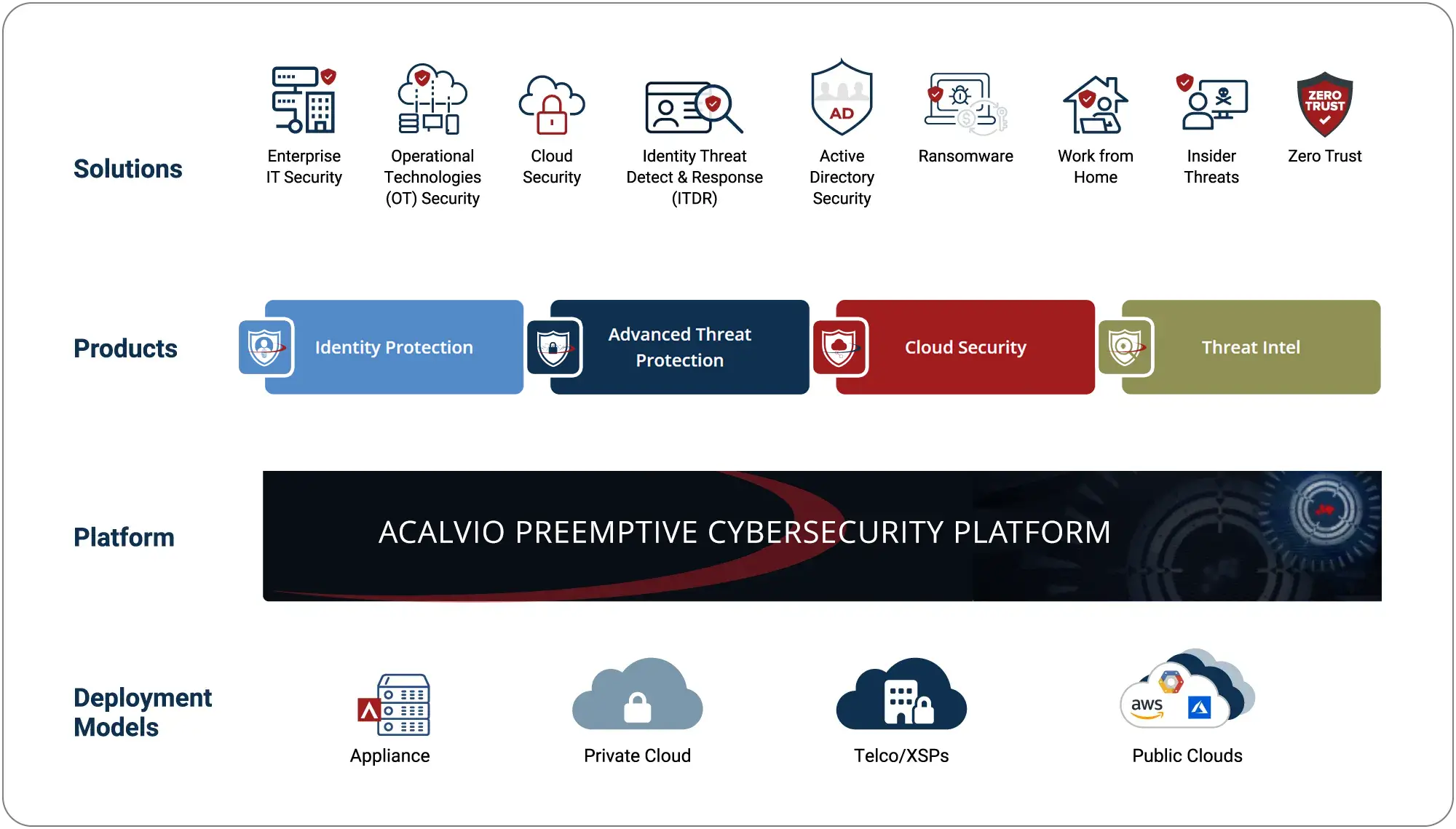
The ShadowPlex platform is the industry’s most comprehensive deception-powered preemptive defense engine. It provides a unified foundation for detecting malicious behavior. With 25+ patents, it combines deception, AI, and seamless integrations to secure IT, OT, identity, and cloud environments.
Why ShadowPlex?
- Deception and AI expose attacks across IT, OT, cloud, and identity environments.
- Decoys and deception redirect attackers away from real assets.
- Connects to SIEM, SOAR, EDR, and XDR for automated response.
- Available as appliance, private cloud, telco/XSP, or public cloud.

Catch attackers early across IT, OT, cloud, and identity.
- Expose threats across IT, OT, cloud, and identity environments.
- Surface credential misuse, lateral movement, and attack staging early.
- Use deception-driven, intent-based detection to avoid false positives.
- Continuously monitor for stealthy, AI-driven and APT threat behaviors.

Redirect attackers into decoys to disrupt their objectives.
- Deploy decoys, breadcrumbs, and honeytokens to attract attackers.
- Derail adversaries by steering them away from production assets.
- Trigger high-confidence alerts on attacker interaction with deception assets.
- Use deception engagement to limit attacker progression and impact.

Feed verified deception alerts into existing SOC tools and workflows.
- Pre-built integrations for SIEM, SOAR, EDR, XDR, and ITSM.
- Streamline alerting, containment, and incident response workflows.
- Enable SOC teams to detect, respond, and automate faster.
- Support for hybrid and multi-cloud security operations ecosystems.

Support global environments everywhere your enterprise operates
Available as appliance, private cloud, or public cloud.
- Scales from small environments to global enterprise deployments.
- No agents required for rapid deployment and minimal disruption.
- AI-powered deception adapts automatically as environments change.
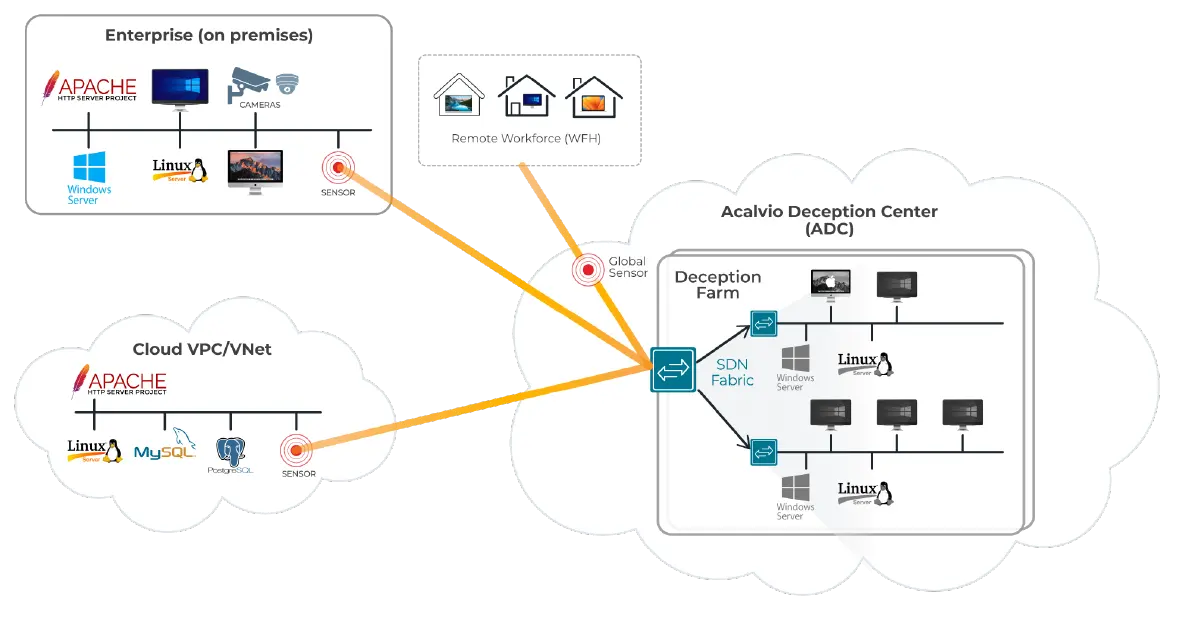
ShadowPlex decoys blend seamlessly into your environment—enabling preemptive detection at scale across IT, OT, and cloud.
Acalvio Deception Center (ADC)
- Centralized brain of the platform
- Hosts, projects, and manages deceptions
- Deployable on-premises or in private/public cloud
Projection Sensors
- Lightweight software sensors for decoy projection
- Installed in enterprise networks and cloud workloads
- Streamline decoy deployment without agents
Protect your environment without agents or complexity.
- Scales deception across IT, OT, identity, and cloud environments
- Eliminates endpoint agents to reduce management overhead
- Lowers software licensing and operational costs
- Provides early threat detection across the entire enterprise

Solves industry tradeoffs between depth and scale.
- Combines low- and high-interaction decoys for broad and deep coverage
- Fluid Deception™ dynamically adjusts to changing environments
- Maximizes detection fidelity without excessive costs
- Scales efficiently across IT, OT, cloud, and hybrid environments

AI-driven automation simplifies and optimizes deployment.
- Auto-designs deception strategies per subnet
- Creates unique, non-finger printable decoys
- Dynamically adjusts to network and infrastructure changes
- Automates alert triage to reduce analyst workload

Pre-built AI-driven playbooks simplify and accelerate deception deployment.
- Encapsulate deception expertise into reusable templates
- Automatically recommend deception types and placement
- Minimize manual effort for faster time to value
- Continuously adapt deception strategy as environments change

Surface only what matters: reduce alert fatigue
- Auto-triage deception events to reduce SOC workload
- Deliver high-fidelity, actionable alerts with minimal noise
- Enable automated containment actions through integrations
- Prevent lateral movement by stopping threats early

Deploy deception at scale—wherever your infrastructure lives.
Key Capabilities:
- Supports native integrations with leading SIEM, SOAR, EDR, and XDR platforms
- Enables agentless deployment across hybrid, multi-cloud, and on-prem environments
- Provides centralized visibility with unified SOC dashboards
- Automates response actions via email, Slack, webhooks, or integrated workflows
Distributed Deception Platforms (DDPs)
KuppingerCole Leadership Compass, Sep 2021
Acalvio Innovation: Setting the Standard for Deception Patents Acalvio leads the industry in deception technology innovation with over 25 granted U.S. patents. Our pioneering work includes advancements in:
- Network neighborhood discovery to map and secure network segments
- AI-driven deception orchestration and autonomous decoy placement
- Automated adversary behavior analysis to generate TTPs and accelerate SOC investigations
- LLM-powered deception Copilot to dynamically create tailored, context-aware decoys
No other deception vendor matches the breadth, depth, or consistency of our patent portfolio. It reflects our mission: to make preemptive, autonomous deception practical at enterprise scale.
Frequently Asked Questions
Deception-Based Preemptive Cybersecurity is a proactive defense strategy that uses deceptive artifacts—such as decoys, honeytokens, and fake credentials—to detect attackers already inside the network. These deception layers operate across endpoints, identity systems, and cloud workloads. Because the decoys have no business value, any interaction is a reliable indicator of malicious activity, enabling early, accurate detection and timely response—before adversaries reach their objectives.
Traditional tools often rely on known signatures or behavior tied to real assets—limiting their effectiveness against unknown threats, insider activity, or credential misuse. Preemptive Cybersecurity adds a new dimension of defense by detecting early-stage attacker activity through interaction with deceptive assets. It provides high-fidelity alerts, improves lateral movement visibility, and reduces dwell time—enabling defenders to act earlier and with greater precision.
Honeytokens are deceptive credentials and data artifacts embedded in legitimate systems, such as OS caches or cloud workloads. Honeytoken accounts are fake user or service accounts. Any interaction with these assets is a high-fidelity indicator of malicious activity—making them essential tools for detecting identity threats like lateral movement and credential misuse.
The Role of Deception Technology in IoT/OT Security
IDC Market Perspective, July 2022
Preemptive Cybersecurity Changes the Game.
Detect attacker tactics early across IT, OT, cloud, and identity—before traditional tools respond.
Deliver high-fidelity, low-noise alerts to reduce investigation time and accelerate response.
Integrate with SIEM, SOAR, EDR, and cloud security platforms for unified threat management.


