Four Pillars of ShadowPlex Advanced Threat Defense
- Surface stealthy recon, credential harvesting, and access staging.
- Detect early indicators of APT and AI-driven attacks
- Expose credential misuse, escalation, and traversal across complex infrastructures.
- Detect Living-off-the-Land tactics used by advanced threat actors.
- Adapt deception to evolving APT and AI-driven attacker behavior.
- Break kill chains before attackers reach critical systems.
- Align early-stage detections to MITRE ATT&CK TTPs for faster response.
- Prioritize defenses based on real attacker progression.

Detect Early APT and AI Reconnaissance
- Detect asset discovery and scanning activities against IT, cloud, and OT environments.
- Surface credential harvesting attempts targeting Active Directory and cloud identity stores.
- Identify early privilege probing and access escalation attempts.
- Expose reconnaissance by both human-led APTs and AI-driven automation.

- Expose credential misuse during lateral traversal across hybrid infrastructures.
- Detect stealthy movement leveraging PsExec, RDP, WMI, and SMB protocols.
- Identify unauthorized access to privileged accounts and sensitive systems.
- Surface multi-stage escalation attempts before they reach critical assets.

- Deploy adaptive deception assets that evolve based on attacker behavior.
- Force AI-driven attacks to engage false targets and reveal tactics.
- Break automated lateral movement and escalation paths mid-chain.
- Slow attacker operations and increase uncertainty inside the network.

- Correlate detected behaviors to MITRE ATT&CK TTPs for rapid investigation.
- Expose progression across initial access, discovery, lateral movement, and escalation techniques.
- Enable faster tuning of defenses aligned to adversary behaviors.
- Prioritize mitigation actions based on real-world attack progression, not theoretical risks.
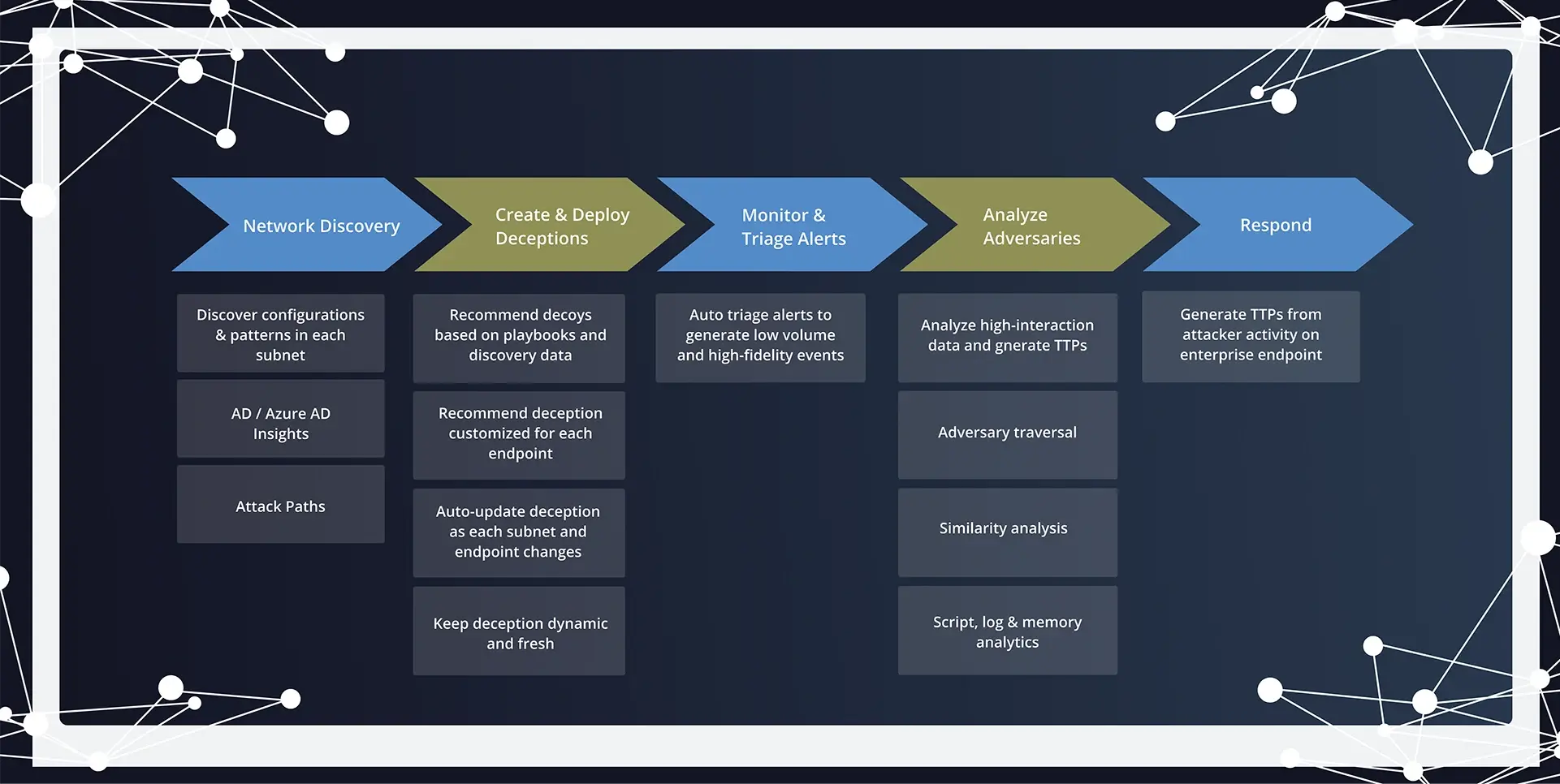
Modern APTs and AI-driven threats adapt faster than traditional defenses can react. ShadowPlex integrates AI into every phase of deception—from network discovery to adversary analysis—enabling dynamic, scalable, and precise early threat detection.
By automating discovery, deployment, triage, and response mapping, ShadowPlex transforms deception from a static tool into an adaptive, high-speed countermeasure against evolving attacks.
Frequently Asked Questions
ShadowPlex uses adaptive deception to surface early attacker behaviors like reconnaissance, credential harvesting, and lateral movement—before they escalate into breaches. Detection focuses on behavior, not static signatures.
Yes. ShadowPlex detects attacker intent and early-stage behaviors that align with MITRE ATT&CK TTPs, even if the specific exploit or malware is new or AI-generated.
No. ShadowPlex operates agentlessly and invisibly across IT, cloud, and OT environments—deploying deception assets without interfering with production traffic or operations.
Built for Advanced Threats. Focused on Preemptive Defense.
Threats Early
- Detect stealthy APT and AI-driven attacks during recon and movement.
- Surface attacker behaviors missed by traditional detection tools.
Attack Chains
- Break lateral movement and escalation paths dynamically.
- Force attackers—human or AI—into early detection traps.
- Deploy agentless deception seamlessly across IT, cloud, and OT.
- Map detections to MITRE ATT&CK for prioritized, real-world defensive tuning.




