- Bait insiders with decoy assets—files, credentials, or systems—to trigger early warning before critical assets are touched.
- Run deception silently in the background without interfering with user workflows, access, or performance.
- Detect file access abuse, unauthorized reconnaissance, lateral movement, and data staging using intent-driven signals.
- Observe and capture behavior that slips past logs and behavior models, without tipping off the insider.

Behavioral models and log analysis aren’t enough. Privileged users can abuse their access slowly, communicate in encrypted channels, or erase traces before anything seems suspicious.
- Privileged insiders exploit trusted access to exfiltrate sensitive data
- Encrypted channels hide command-and-control traffic
- Low-and-slow offensive tactics keep insiders under the radar
- Deleted logs obscure malicious activity
The Four Pillars of Insider Threat Detection with Deception
- Plant decoy credentials and traps to detect lateral movement and data access by trusted users acting maliciously.
- Uncover silent exploration behavior as insiders map file shares, probe directories, or catalog sensitive systems.
- Identify activity that blends into daily operations—deception triggers when users touch what they shouldn’t.
- Deception triggers when users touch what they shouldn’t — deception interactions confirm intent, eliminating false positives and escalating only what truly matters.
Catch trusted users misusing legitimate access.
- Plant deceptive credentials and files to lure insider interaction
- Trigger alerts when privileged accounts attempt unauthorized access
- Surface intent-driven behavior that bypasses policy-based detection
- Detect early-stage reconnaissance on sensitive internal assets

Uncover exploration behavior that precedes data theft.
- Deploy decoys in file shares, directories, and systems
- Detect unauthorized mapping of sensitive assets
- Identify probing of access controls and data structures
- Catch insiders silently cataloging what’s worth stealing

Expose insider that blends into normal operations.
- Detect gradual credential misuse and lateral movement
- Surface irregular access to decoy files over time
- Identify long-dwell threats without behavioral baselines
- Uncover staged access patterns before data is exfiltrated

Reduce noise with signals rooted in adversary intent.
- Alert only on interaction with deceptive assets
- Eliminate false positives from normal user behavior
- Provide clear context for rapid triage and investigation
- Feed high-confidence signals into SIEM and SOAR workflows

Insider threats come in many forms—and not all are malicious. From careless mistakes to coordinated data theft, insider activity can bypass traditional defenses that rely on external indicators of compromise.
Key Threat Categories
- Unintentional: Accidental actions by employees or contractors that expose sensitive data
- Intentional: Privileged users exploiting access to steal data or disrupt systems
- Other: Third-party or collusive threats with access to critical environments

Insiders don’t break in, they log in, making them hard to detect
- Use of valid credentials hides intent
- Actions blend into normal workflows
- Logs can be deleted or manipulated
- Behavior-based models miss stealthy or low-volume activity
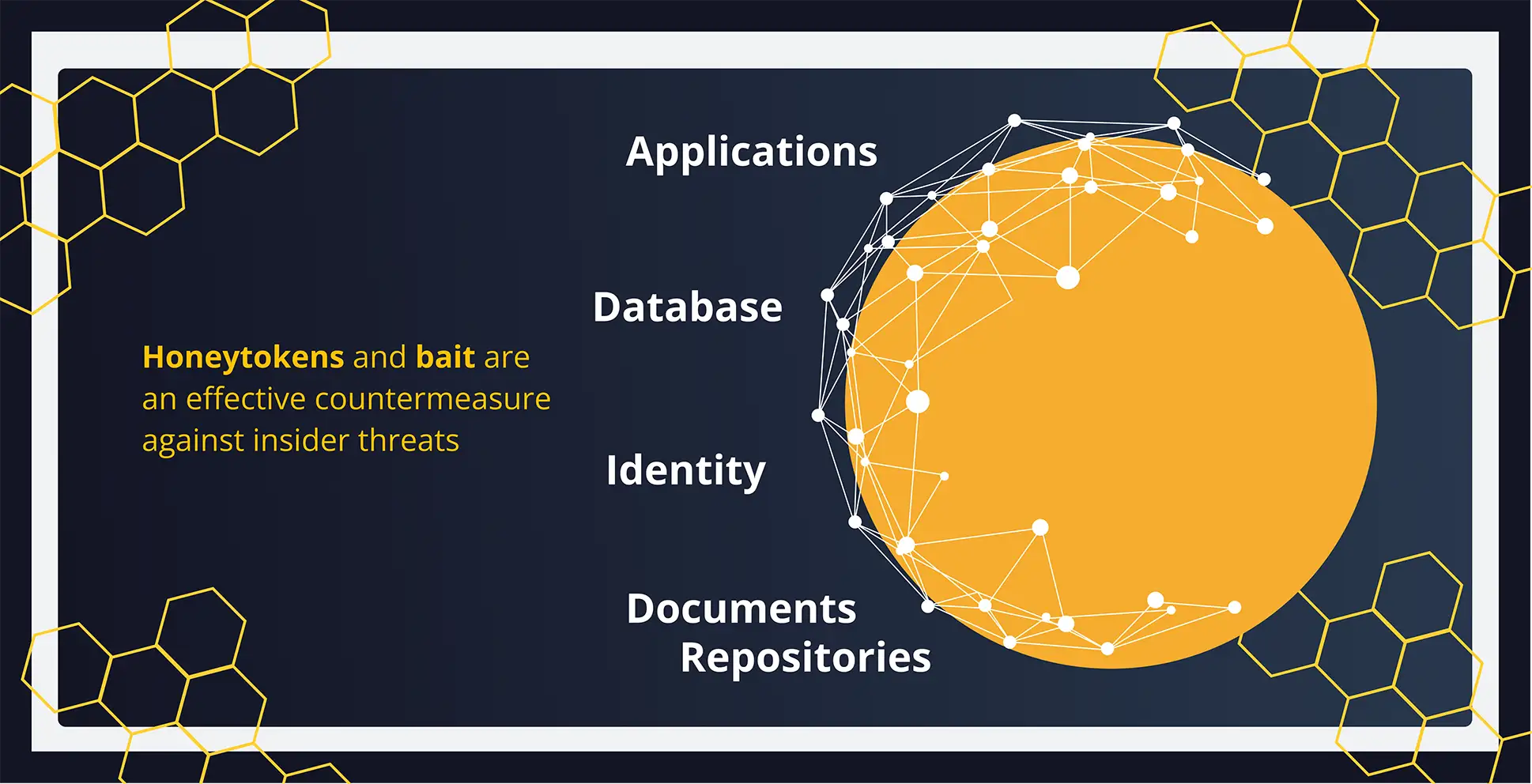
Acalvio plants realistic, enterprise-aligned honeypots and honeytokens across sensitive systems, without disrupting operations.
These deceptive artifacts mimic real assets, such as:
- Applications: Fake logins and service credentials to trap insiders targeting business apps
- Databases: Embedded credentials and decoy queries to expose data access misuse
- Identities: Deceptive accounts and tokens to detect lateral movement and privilege abuse
- Document Repositories: Fake files to catch exfiltration and unauthorized snooping
Each interaction with a deception asset provides high-fidelity, intent-driven alerts—giving security teams the context they need to investigate fast and respond precisely.
Preemptive Cybersecurity Changes the Game for Insider Threat Defense.
Surfaces malicious insider behavior by triggering alerts only when high-value decoys are touched, eliminating guesswork and noise.
Gain visibility into credential abuse and unauthorized access without relying on invasive monitoring or brittle behavioral baselines.
Get early, high-fidelity signals of intent so you can investigate and contain insider threats before damage escalates.
Frequently Asked Questions
Insider threats are individuals within an organization who, intentionally or unintentionally, misuse their access to cause harm. This can lead to significant consequences, including data breaches, financial losses, and damage to the organization’s reputation. These threats are particularly concerning because insiders have direct access to sensitive information and systems, making it easier for them to carry out their activities unnoticed.
Traditional security solutions are insufficient for detecting insider threats because they rely on signature and behavior-based detection methods. While these methods can identify unusual activities, they often miss the context-specific nuances of insider threats. In addition, traditional approaches can produce numerous false positives, overwhelming security teams and leading to alert fatigue.
Cyber deception is agnostic to the specific tactics, techniques, and procedures that a threat uses. When it comes to detecting insider threats, cyber deception does not have the limitations of signature and behavior-based detection solutions.

