- Deploy deception across AD, Entra ID, and cloud IAM to detect credential misuse before escalation.
- Reveal attacker activity that occurs between Zero Trust policy enforcement points.
- Catch misuse of elevated credentials and service accounts with decoys that trigger intent-based alerts.
- Add early detection and containment to strengthen alignment with CISA and DoD Zero Trust frameworks.

Detect advanced threats without relying on known attack signatures.
- Use decoys and lures aligned to attacker mission objectives.
- Reveal stealthy lateral movement and identity misuse.
- Trigger high-fidelity alerts without noisy baselining.
- Uncover threats early in the attack path.
Reduce noise while accelerating response.
- Eliminate false positives with intent-driven alerts.
- Automate isolation workflows based on verified activity.
- Reduce manual triage with pre-correlated deception events.
- Improve analyst focus on true positives.

Actively surface hidden threats inside your environment.
- Guide hunters to high-risk paths with deception telemetry.
- Validate hypotheses with adversary interaction data.
- Continuously monitor for suspicious behavior on dormant assets.
- Enable iterative hunts based on attacker behavior.
Strengthen identity security with deception-powered detection.
- Detect identity misuse across hybrid identity infrastructure.
- Protect service accounts, AD credentials, and cloud IAM tokens.
- Generate real-time alerts when credentials are probed or used.
- Reveal privilege escalation attempts before impact.

Extend visibility and detection to blind spots.
- Detect attacks from unmanaged BYOD, IoT, and OT systems.
- Place decoys to mimic unmanaged assets for early warning.
- Enable coverage without requiring agents or sensors.
- Stop threats from propagating into protected environments.

Expose internal misuse with high-fidelity detection.
- Monitor for unusual access to deceptive files and shares.
- Reveal insider intent without relying on behavior profiling.
- Detect slow-moving data exfiltration activity.
- Support fast, discreet investigations with concrete evidence.
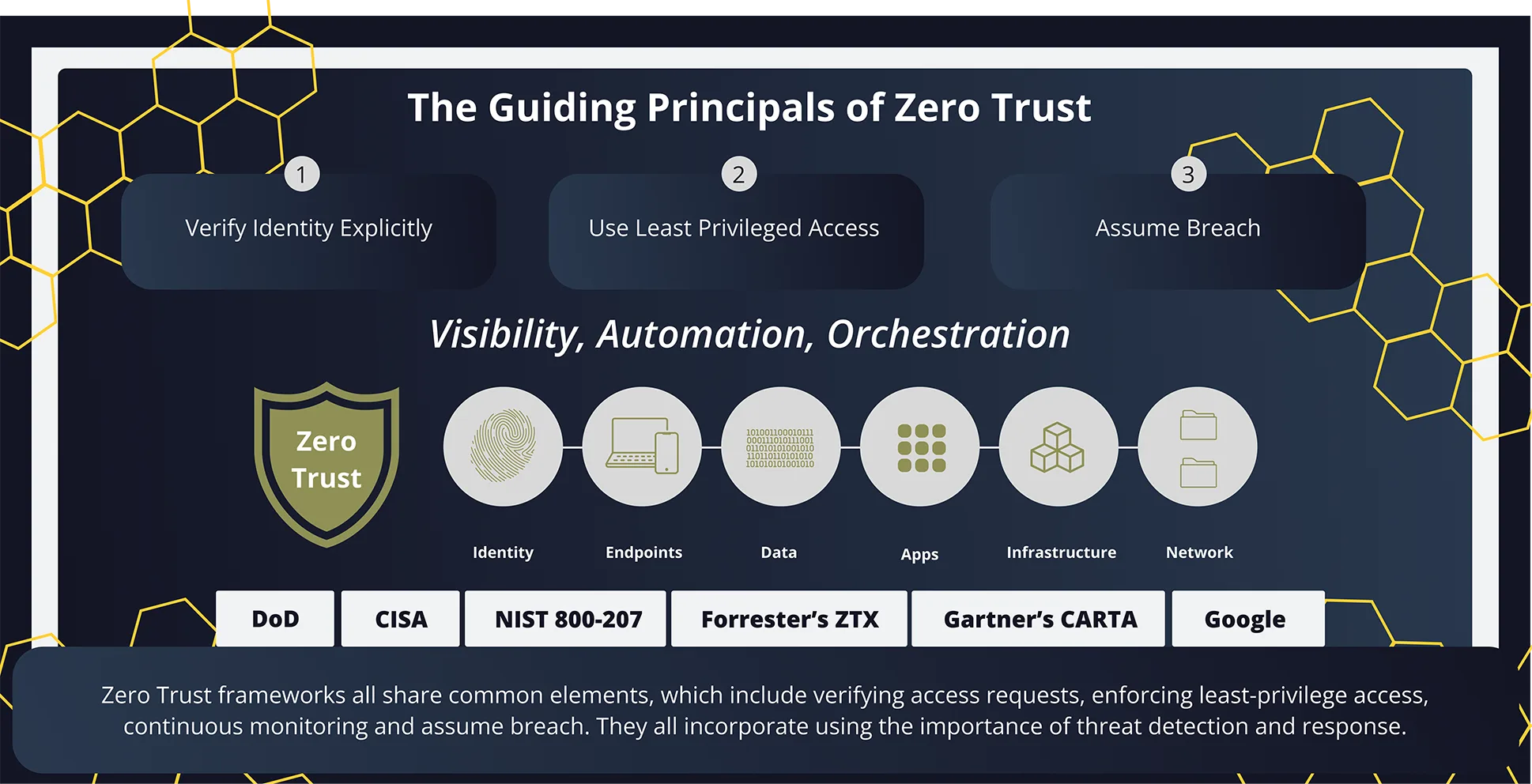
Zero Trust frameworks all share common elements, which include verifying access requests, enforcing least-privilege access, continuous monitoring and assume breach. They all incorporate using the importance of threat detection and response.
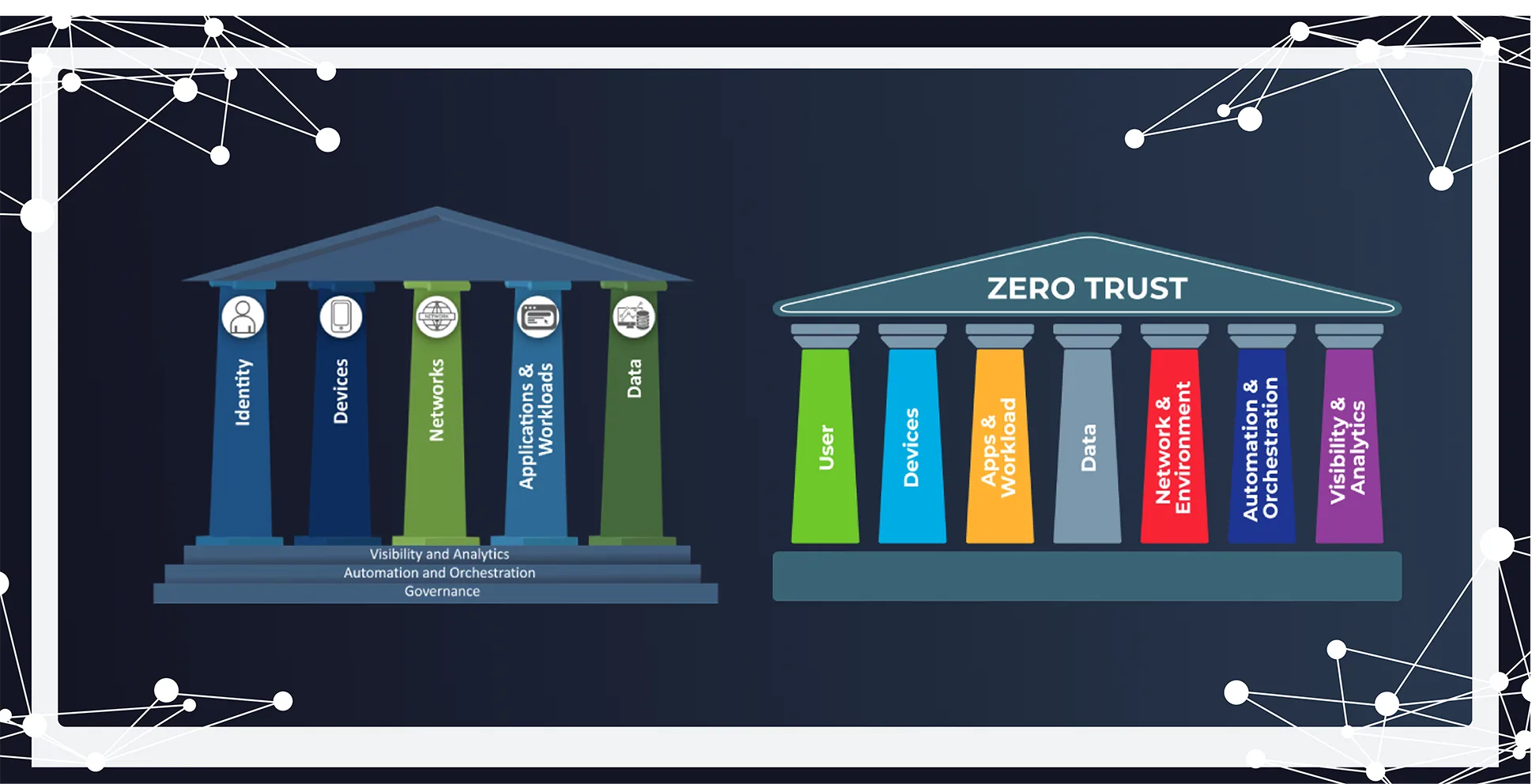
The DoD framework has seven pillars and the CISO model has five pillars and provides a maturity model.
DOD: Zero Trust Pillars
The DoD zero trust pillars provide the foundational areas for the DoD zero Trust Security Model and the DoD Zero Trust Architecture.
CISA: Zero Trust Maturity Model
Each pillar includes general details regarding the following cross-cutting capabilities: visibility and analytics, automation and orchestration, and governance.
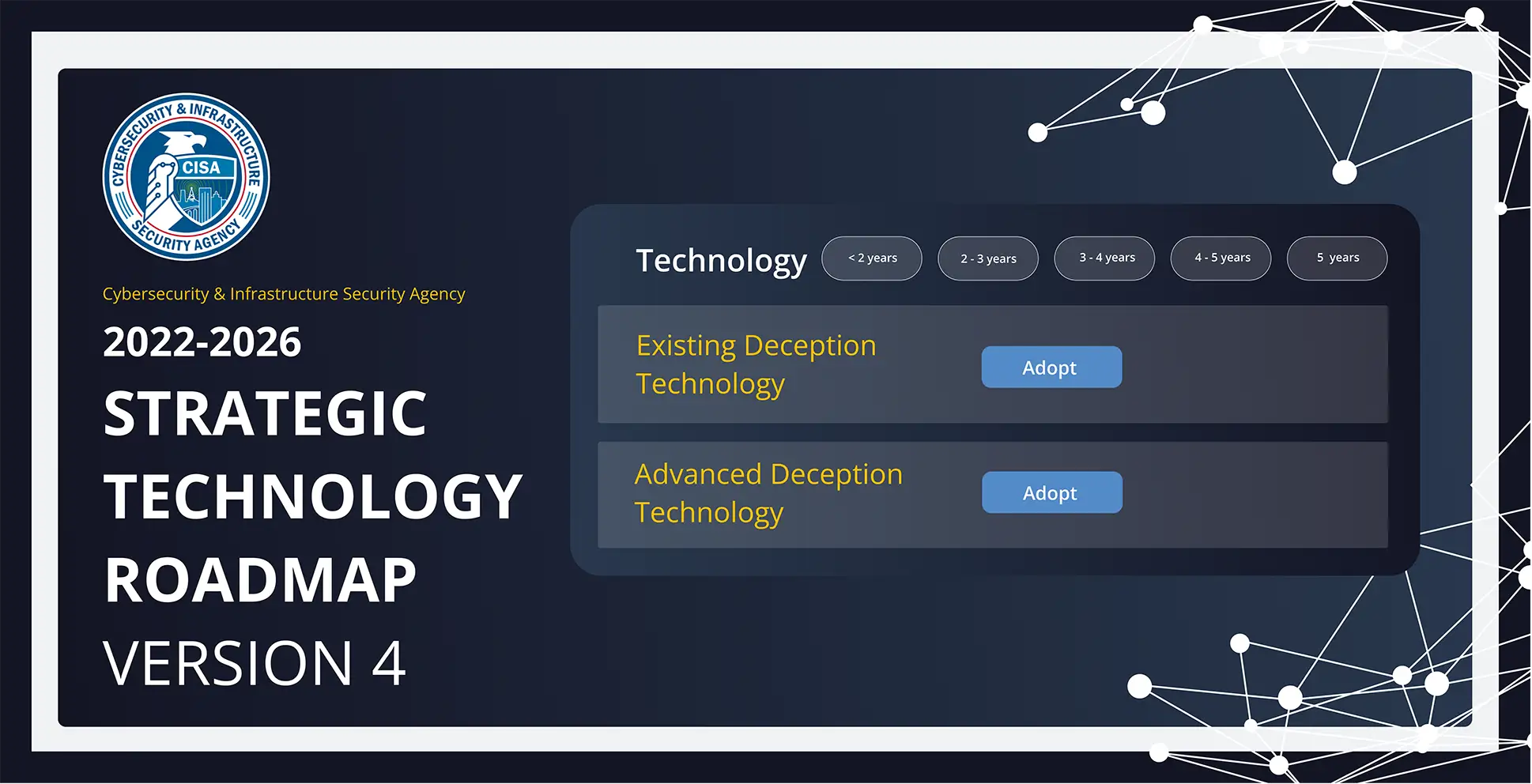
CISA published top recommendations in its 2022-2026 Strategic Technology Roadmap. The recommendation is to adopt Deception Technology strategies within the next two years.
Zero Trust and Preemptive Cybersecurity with Deception
Detect threats that bypass identity and policy controls—without requiring prior knowledge or baselines.
Trigger high-fidelity alerts on real attacker activity and automate response to isolate threats before damage occurs.
Gain coverage across managed, unmanaged, and hard-to-monitor systems—without agents or added infrastructure.
Frequently Asked Questions
Acalvio enhances Zero Trust by adding intent-based detection between policy enforcement points—revealing credential misuse, lateral movement, and privilege abuse that identity controls may miss.
No. Acalvio integrates with your existing IAM, AD, and cloud identity systems without disrupting authentication flows or requiring changes to policies.
Yes. Deception generates high-fidelity signals based on adversary engagement—not behavior modeling or log correlation—making it ideal for environments where visibility is fragmented.



