- Products
-
ProductsPlatform
- ShadowPlex Advanced Threat Defense
Deception for early detection of cyber threats with precision and speed
- ShadowPlex Identity Protection
Visibility, management and protection of identity stores and attack paths
- Acalvio Active Defense Platform
Comprehensive and Award-winning Distributed Deception Platform
- What is Active Defense?
Active defense detects and diverts attacks.
- Why do I need Acalvio Active Defense?
Active Defense deceives and disrupts attackers.
- ShadowPlex Advanced Threat Defense
-
- Solutions
-
Technology SolutionsIndustry Solutions
- Breach Detection
Active Defense for breach detection and response, both in on-premises and cloud workloads
- Identity Threat Detection & Response
Visibility into Identity attack surface and effective detect & respond solution for identity attacks
- OT / ICS Security
Passive and low-risk agentless solution that is easy to deploy
- Active Directory Protection
Visibility into AD attack surfaces and detection of AD Attacks
- Threat Hunting
Active threat hunting, based on targeted deception, to confirm hunting hypothesis
- Ransomware
AI-Driven Advanced Deception Technology to combat even zero-day Ransomware
- Honeytokens for CrowdStrike
Honeytokens are deceptive credentials and data that are embedded in legitimate assets
- Zero Trust
Zero trust is a security model that assumes that no one inside or outside of the network can be trusted
- Public Sector
Targeted solution for protecting Federal agencies in conformation with NIST and CISA recommendations
- Healthcare
Active defense solutions thwart healthcare attacks before they can inflict real damage.
- Breach Detection
-
- Resources
- Partners
- Company
Botnet
What Is a Botnet?
A botnet, short for “robot network,” is an intricate web of interconnected devices, referred to as “bots” or “zombies.” These devices, often computers or IoT/IIoT devices, have been hijacked and infected with malicious software, transforming them into obedient foot soldiers at the command of a central authority.
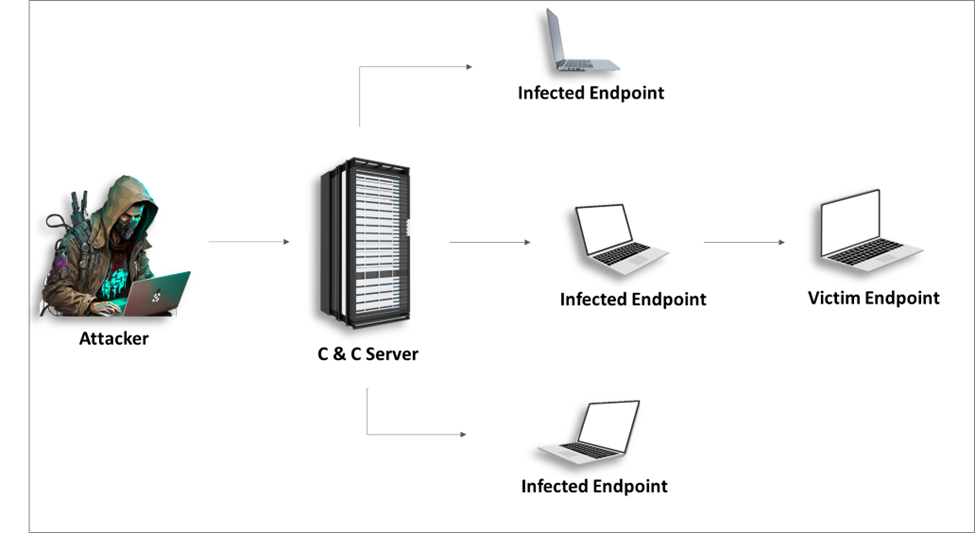
What Are the Methods of Botnet Propagation?
Botnets propagate through various methods, using some of the primary methods described below:
Exploitation of Vulnerabilities:
Cybercriminals exploit known software vulnerabilities in target devices, gaining unauthorized access to implant bot software and subjugating them to the botnet.
Social Engineering and Phishing:
Deceptive tactics, such as phishing emails with malicious attachments or links, can coerce users into unwittingly installing bot software on their devices.
Drive-by Downloads:
Malicious code concealed on compromised websites takes advantage of visitors’ vulnerable systems, covertly downloading bot software without their knowledge.
Trojan Horse Techniques:
Some botnets are distributed through Trojan horse programs that disguise themselves as legitimate software, only to unleash bot software upon installation.
How Do Botnets Work?
Botnets are formidable tools for unleashing cyber attacks with widespread impact. These networks of compromised devices, under the control of a single entity, can execute a variety of malicious activities.
Botnets launch Distributed Denial of Service (DDoS) attacks by overwhelming targets with a barrage of traffic, rendering services inaccessible. They spread malware by sending malicious emails or exploiting vulnerabilities, initiating data breaches and ransomware infections.
Botnets also engage in credential stuffing, using stolen passwords to compromise accounts. Additionally, they exploit compromised devices to mine cryptocurrencies, creating financial gain for attackers.
Their agility and ability to coordinate attacks make botnets a persistent and evolving threat to digital infrastructure and data security.
What are the Different Types of Botnet Attacks?
Distributed Denial-of-Service (DDoS) attacks
This is the most common type of botnet attack. In a DDoS attack, the botnet sends a flood of malicious traffic to a target website or server, causing it to become overwhelmed and unavailable.
Malware distribution
Botnets can be used to distribute malware, such as viruses and trojans. This malware can then be used to steal data, install other malware, or take control of the victim’s device.
Phishing attacks
Botnets can be used to send phishing emails or text messages. These emails or text messages often appear to be from a legitimate source, such as a bank or credit card company. When the victim clicks on a link in the email or text message, they are taken to a fake website that looks like the real website. After the victim enters their personal information on the fake website, the attacker can steal it.
Click fraud
Botnets can be used to click on ads on websites. This can generate revenue for the attacker, as the advertiser is charged each time their ad is clicked on.
Censorship circumvention
Botnets can be used to circumvent censorship by bypassing blocks on websites or social media platforms. This can be used to spread propaganda or to access information that is not available in the victim’s country.
Stealth mining
Botnets can be used to mine cryptocurrency without the victim’s knowledge. This can drain the victim’s battery and use up their bandwidth.
The Growing Threat of Botnets
Predicted botnet threats pose a significant concern in the evolving cybersecurity landscape. As these malicious networks grow more sophisticated, they’re expected to leverage artificial intelligence and machine learning to enhance attack strategies, making them even harder to detect and combat.
The infiltration of Internet of Things (IoT) devices is likely to rise, exploiting their weak security. Botnets may collaborate with other malware for more devastating combined attacks. Political and geopolitical motivations could drive botnets to influence public opinion or disrupt critical infrastructure.
Supply chain attacks might exploit vulnerabilities within software vendors or service providers. Despite ongoing efforts to counter botnets, their adaptability and innovation continue to pose substantial risks to digital ecosystems.
Traditional security solutions often struggle to effectively detect and prevent botnet attacks due to the dynamic and evolving nature of these threats. Botnets employ sophisticated tactics, leveraging encryption, obfuscation, and decentralized command structures to evade signature-based detection methods.
Their distributed nature makes them harder to pinpoint, as individual compromised devices may exhibit seemingly benign behavior. Moreover, the sheer scale of botnets enables them to overwhelm traditional security defenses, such as firewalls and antivirus software.
Additionally, the increasing use of zero-day exploits and polymorphic malware allows botnets to exploit vulnerabilities before security patches can be applied. These factors collectively undermine the efficacy of conventional security measures, necessitating the adoption of advanced and adaptive strategies to effectively combat botnet attacks.
Can Acalvio Be Used to Enable Botnet Protection in the Enterprise?
Acalvio’s Advanced Deception Technology offers a powerful approach to mitigating botnet threats by diverting and misleading attackers, thereby minimizing their ability to infiltrate and propagate within a network. By deploying deceptive elements like decoys, files, and credentials, organizations can create a virtual minefield that misleads and distracts botnets.
When bots interact with these decoys, security teams receive early alerts, enabling rapid response and containment. Furthermore, deception technology enhances threat detection by capturing attacker tactics, techniques, and procedures, facilitating in-depth analysis and proactive countermeasures.
It effectively disrupts botnet communication channels, exposes their presence, and hinders their lateral movement, substantially impeding their ability to carry out malicious activities and reducing the potential impact of botnet-driven attacks.
For more information about how Acalvio can be used to protect against cybersecurity threats like botnets, check our Advanced Threat Defense product.