Passive Defense vs Active Defense
Cyber security defenses can be passive or active. Passive solutions focus on “denial”; essentially denying access to an asset when an attack against it is detected. Active Defense cyber security proactively detects and diverts attacks and engages the adversary to learn the attack tactics, techniques, and procedures (TTPs). It is also about dynamically changing the network landscape or the attacker’s perception to detect and mitigate attacks early.
| Passive Defense (Denial) | Active Defense (Deception) | |
| Endpoint | Detect and block suspicious activity on endpoint elements. | Introduce deception elements (breadcrumbs and baits) into the endpoint to feed deception data and redirect attacks. |
| Network | Detect and block suspicious lateral movement to network elements. | Introduce deception assets into the network to engage with the attackers and collect TTPs. |
| Identity | Detect and block suspicious access attempts to identities / Active Directory. | Introduce deception identities (on endpoints and in Active Directory) to slow down and redirect attacks. |
MITRE Engage
MITRE Engage is a knowledge base for Active Defense and adversary engagement. It’s no surprise that MITRE Engage features deception technology as the most effective solution for adopting an Active Defense strategy. Deception technology is the perfect choice because deceptions can be used to detect and respond to malicious activities, without affecting legitimate traffic and transactions.
Cyber Deception detects threats by overlaying a fabric of pervasive deceptions across the enterprise network. Deceptions are not part of the enterprise business processes and systems. So, any interaction with a deception generates a high-fidelity alert. This form of threat detection, which can detect even zero-day exploits, is increasingly acknowledged as an important cyber security defense layer.
Cyber deception has been around for a couple of decades mostly as honeypots – cleverly crafted fake computing resources, placed as to seem part of the enterprise IT network and containing valuable information. Honeypots, though effective, have been difficult to deploy at scale and to manage by keeping them fresh and relevant.
The state of cyber deception has evolved significantly in the recent years. ShadowPlex is a state-of-the-art distributed deception platform, which can automatically deploy thousands of deceptions corresponding to any network element, across distributed and hybrid enterprise networks.
Deception is NOT just Honeypots
ShadowPlex cyber deception provides a comprehensive deception palette that includes decoys (also called honeypots), breadcrumbs, baits, Honey Accounts, and Honeytokens. These deceptions are blended into and deployed throughout the distributed (and hybrid) network, on enterprise endpoints, and in credential stores such as Active Directory. Legitimate users of the organization will not look for or try to use a deployed deception. So, an alert generated by an adversary accessing a deception is a high-fidelity alert.
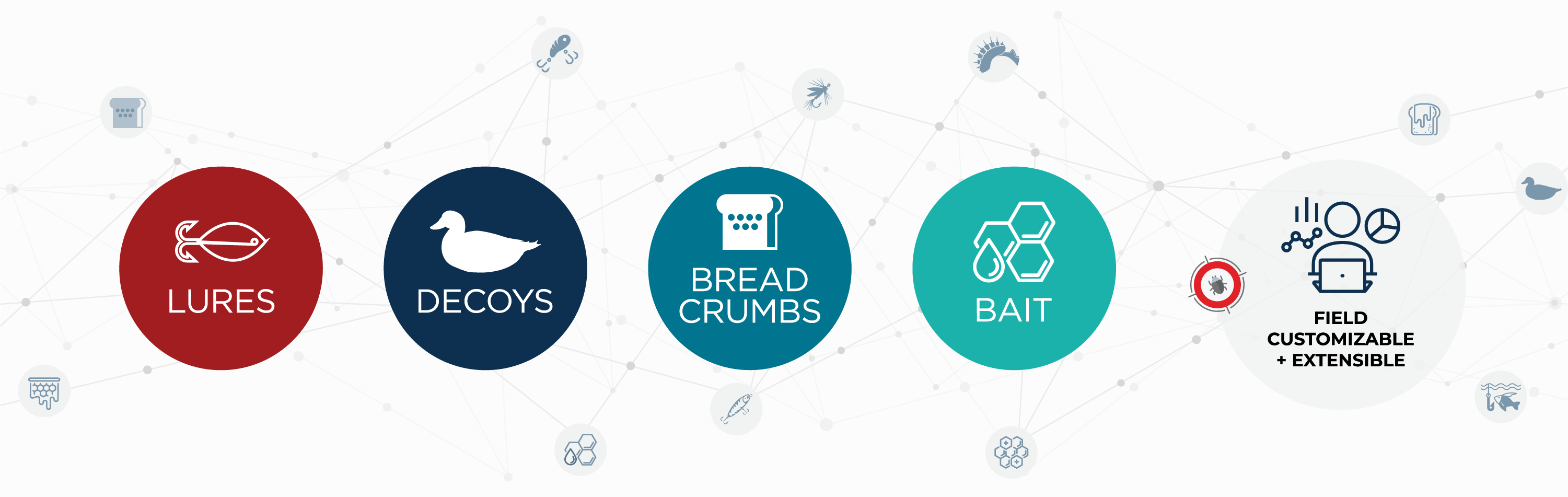
Start with Decoy Types
Low Interaction Decoys
- Network services and applications
- Attacker cannot login
- Often done via emulation leading to lower quality decoys
- Can deploy many decoys
High Interaction Decoys
- Real VM Hosts, Applications, Database Servers, Shares
- Attacker can login – full interaction decoys that provide deeper engagement
Make Decoys Attractive
Introduce weaknesses in decoys to make them attractive
Vulnerabilities in OS, applications, protocols
Weak configurations and permissions
Deception service accounts for important apps
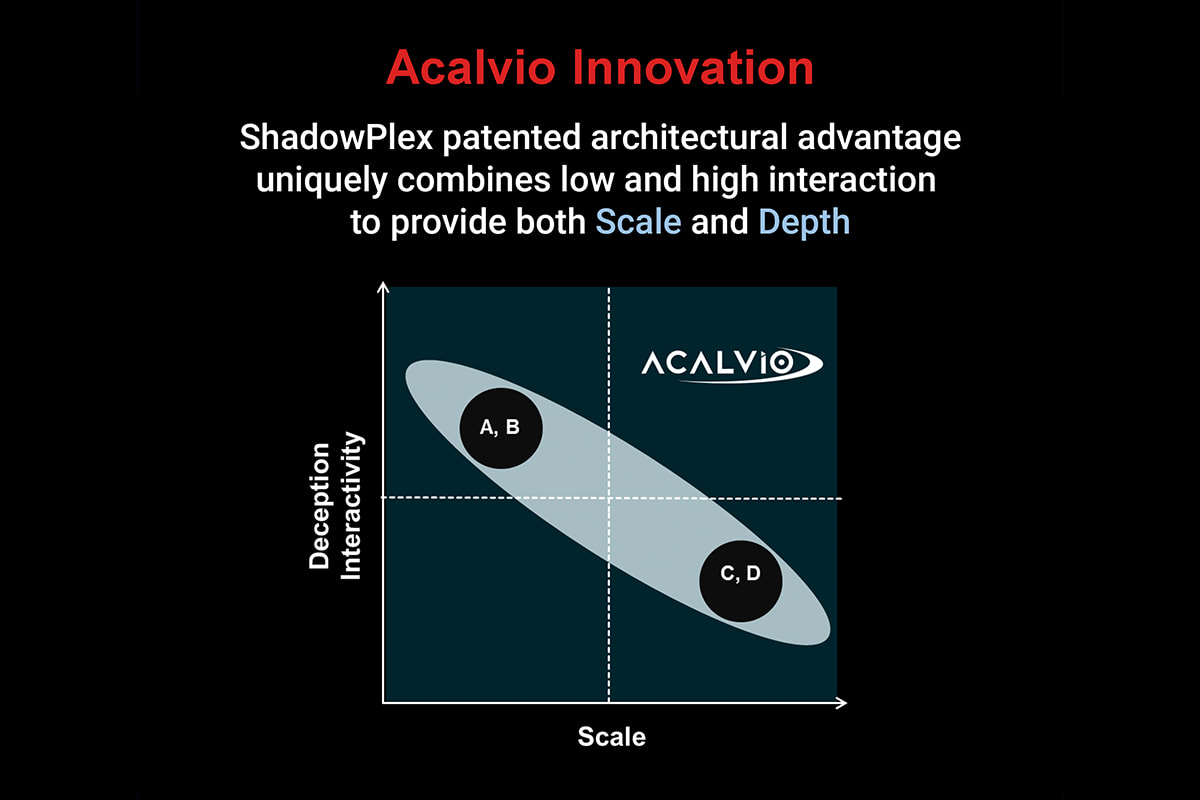
Acalvio Innovation
- Extensible framework for the customer to add custom decoys


Lead Attacks to Decoys
Many uses for Breadcrumbs / Baits
- Act as micro-sensors
- Display (mis)information
- Redirect attacks to decoys
Acalvio Innovation
- Completely automated configuration, deployment and management of breadcrumbs and baits
Blend Deception
Deception needs to blend into the environment continuously to be effective
- Networks can change
- Adversary behavior will change
- Threats will change
Acalvio Innovation
- Integrated AI keeps track of network neighborhood and endpoint settings across the enterprise and automatically blends deceptions.

Keep Cyber Deception Dynamic

Static Deceptions
- Hardly changes
- Easy to fingerprint & avoid

Acalvio Innovation: Dynamic Deceptions
- Continuously updated to fit the neighborhood
- Hard to identify or fingerprint
Automate, Automate, Automate
Deception technology has been proven to work, but it has remained mainly in the research world for decades. The primary reason is that deployment and management of effective and enterprise-scale cyber deceptions cannot be done manually. Deceptions have to be present in every subnet and multiple endpoints for early detection of attacks – we are looking at thousands of decoys and deceptions on tens of thousands on endpoints. Deception definition must be automated. The Security team cannot be expected to study assets in the neighborhood and then define deceptions. Deceptions must blend into every part of the network and always be relevant. Artificial Intelligence (AI) is the only way to realize the promise of cyber deception.
How does deception-based Active Defense work?
End-user breach example
Phishing
- Initial foothold
- Attacker has remote command & control
- Initial recon
Establish Additional Beachheads
- Redundancy
- Sacrificial lambs
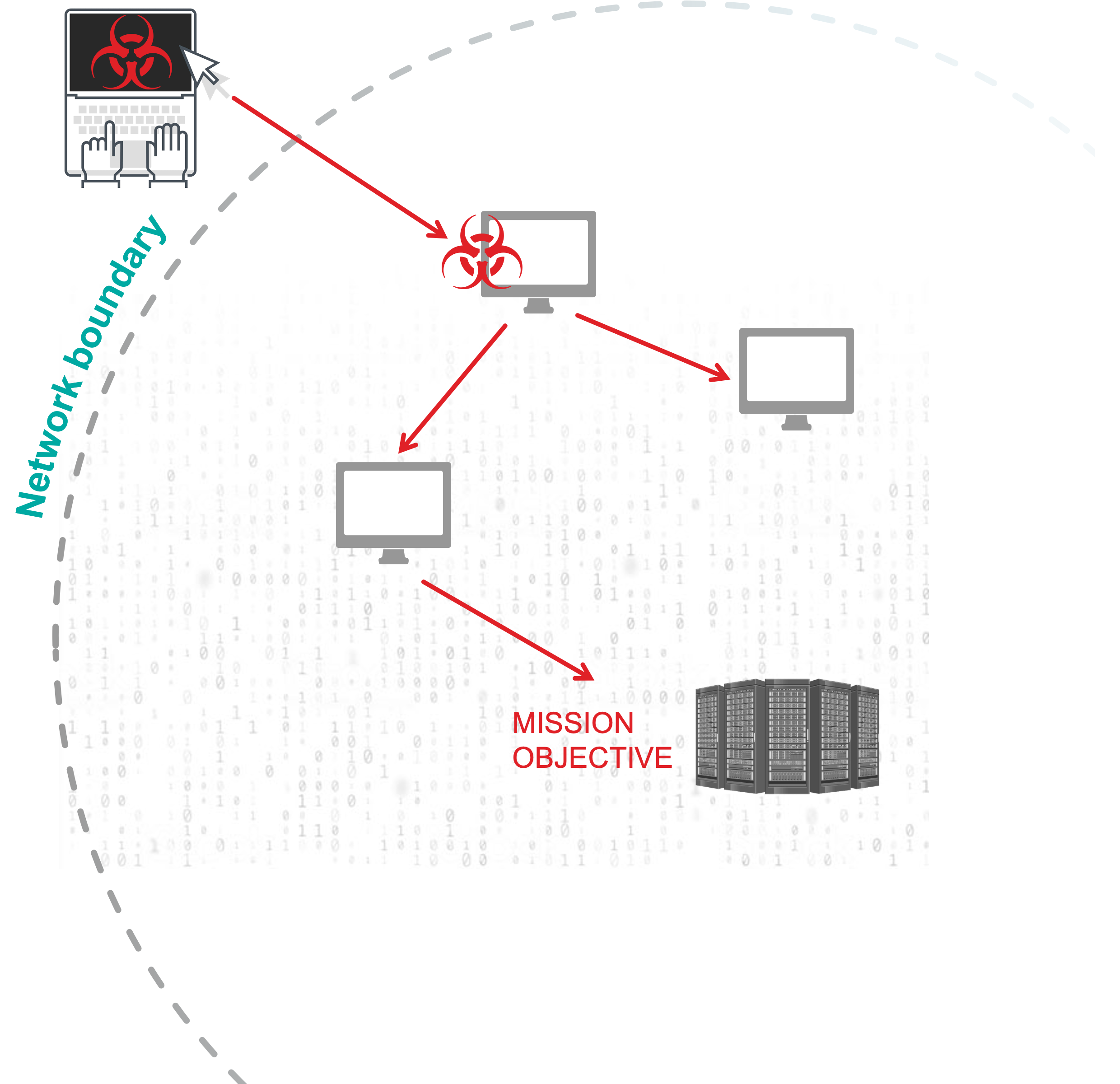
Lateral move towards Mission Objective(s)
- Data exfiltration
- Disruption
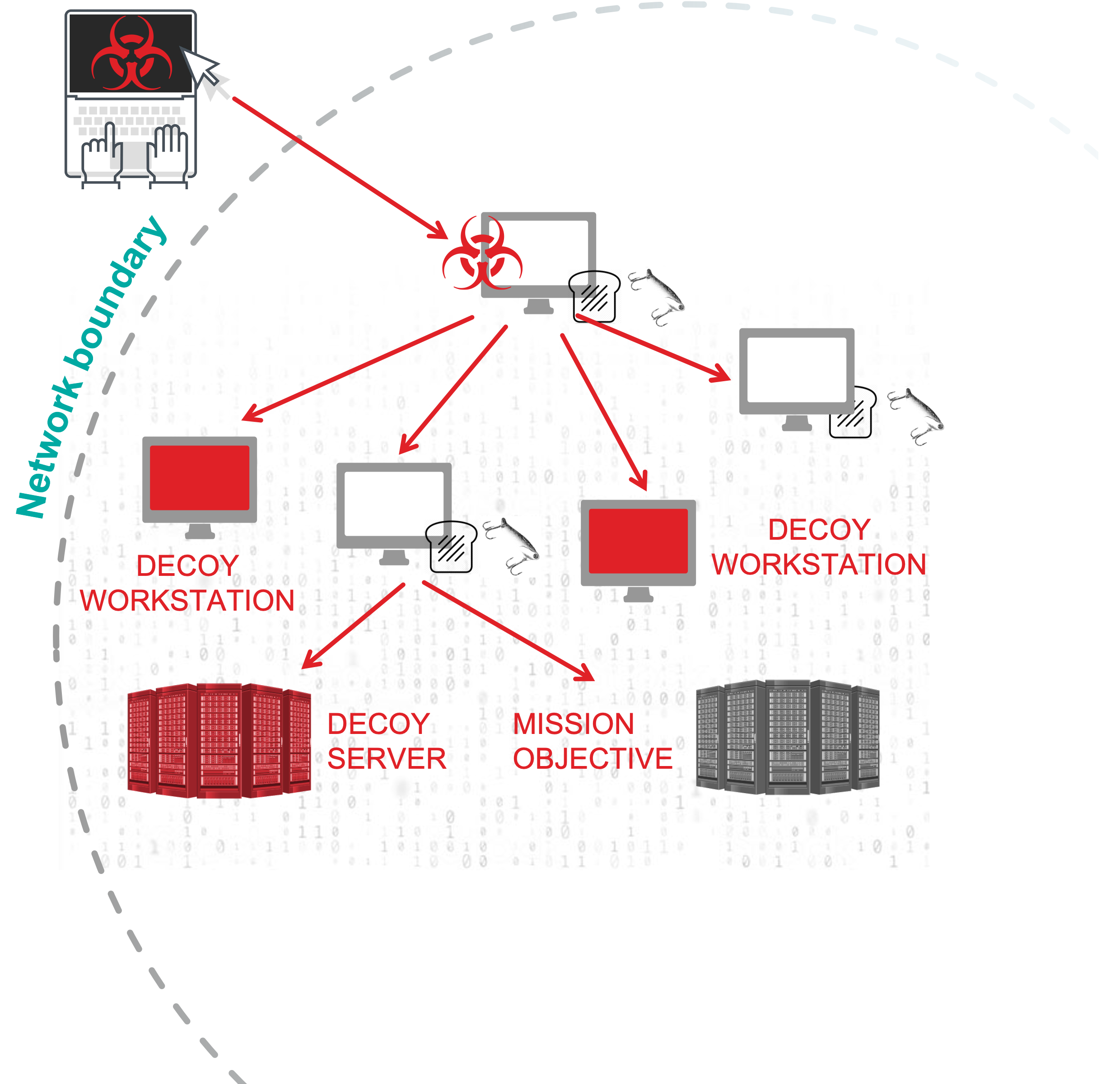

Decoys
- Dense Minefield
- Detect Adversary as Beachheads Established

Breadcrumbs
- Present False Trail
- Deceive Adversary During Recon
- Divert Away from Mission Objective to Decoy

Baits
- Tripwires
Proactive cyber defense based on deceptions provides a completely different way to detect attacks. It complements and augments existing security solutions that are based on signatures and behavioral models. Cyber deception has proven to be very effective, but the first-generation solutions had limitations. Acalvio solved the limitations with innovative technology that enables enterprise scale and autonomous deception.
Please follow the “Read More” link to understand why you need Active Defense when you have other security solutions already deployed in your enterprise network.
Why is Active Defense Important?
The importance of Active Defense lies in its ability to protect organizations from sophisticated cyber threats that traditional security measures cannot detect. It is a proactive approach that continuously detects and responds to threats in real time, enabling organizations to respond quickly and effectively to security incidents, thereby reducing the impact of a breach. Active Defense improves an organization’s security posture by identifying vulnerabilities and weaknesses, helping the organization save money by reducing the cost of cleaning up after a breach, protecting their reputation by minimizing the impact of a breach, and helping them meet compliance requirements. Active Cyber Defense plays a critical role in helping organizations stay ahead of cyber threats.
Strengthening Cybersecurity with Acalvio’s Active Defense
Active Defense provided by Acalvio can be used to detect threats in real time, enabling organizations to respond quickly and effectively to security incidents. The Acalvio solution combines artificial intelligence and Acalvio’s cybersecurity domain expertise to provide advanced threat detection and response capabilities. In addition, the Acalvio solution provides comprehensive visibility across the attack surface and actionable insights, which help organizations improve their security posture and reduce the risk of attacks.
FAQs:
How is Active Defense evolving, and what can we expect to see?
How is Active Defense used in cybersecurity?
How does deception technology fit into an overall network security strategy?
What are the different types of deceptions and their motivations?
How can organizations deploy and manage Active Defense cyber security measures effectively?
What is an example of Active Defense using deception technology?
Next Steps
Explore our patented technologies to enable Active Defense and Identity Protection in your enterprise.