- Products
-
ProductsPlatform
- ShadowPlex Advanced Threat Defense
Deception for early detection of cyber threats with precision and speed
- ShadowPlex Identity Protection
Visibility, management and protection of identity stores and attack paths
- Acalvio Active Defense Platform
Comprehensive and Award-winning Distributed Deception Platform
- What is Active Defense?
Active defense detects and diverts attacks.
- Why do I need Acalvio Active Defense?
Active Defense deceives and disrupts attackers.
- ShadowPlex Advanced Threat Defense
-
- Solutions
-
Technology SolutionsIndustry Solutions
- Breach Detection
Active Defense for breach detection and response, both in on-premises and cloud workloads
- Identity Threat Detection & Response
Visibility into Identity attack surface and effective detect & respond solution for identity attacks
- OT / ICS Security
Passive and low-risk agentless solution that is easy to deploy
- Active Directory Protection
Visibility into AD attack surfaces and detection of AD Attacks
- Threat Hunting
Active threat hunting, based on targeted deception, to confirm hunting hypothesis
- Ransomware
AI-Driven Advanced Deception Technology to combat even zero-day Ransomware
- Honeytokens for CrowdStrike
Honeytokens are deceptive credentials and data that are embedded in legitimate assets
- Zero Trust
Zero trust is a security model that assumes that no one inside or outside of the network can be trusted
- Public Sector
Targeted solution for protecting Federal agencies in conformation with NIST and CISA recommendations
- Healthcare
Active defense solutions thwart healthcare attacks before they can inflict real damage.
- Breach Detection
-
- Resources
- Partners
- Company
CVE (Common Vulnerabilities and Exposures)
What is a CVE?
CVE stands for “Common Vulnerabilities and Exposures.” It is a list of publicly disclosed cybersecurity vulnerabilities that is free to search, use, and incorporate into products and services. CVE helps vendors and researchers identify, define, and catalog vulnerabilities in a standardized way.
Each CVE entry is assigned a unique identifier, known as a CVE ID, which consists of the year the vulnerability was assigned, followed by a sequential number (e.g., CVE-2023-12345). This identifier helps in referencing and discussing specific vulnerabilities across different platforms and sources.
Difference Between Vulnerability and Exposure
A vulnerability is a weakness or flaw in a system, software application, or hardware component that can be exploited by attackers to compromise the confidentiality, integrity, or availability of the system or its data.
Exposure refers to the condition in which a system or software application is at risk due to the presence of a known vulnerability. An exposed system is susceptible to attacks that could take advantage of the identified vulnerability to compromise its security. Exposure implies that the vulnerability is present and can be exploited by attackers.
Benefits of CVEs
The Common Vulnerabilities and Exposures system plays a crucial role in enhancing cybersecurity by standardizing vulnerability information, promoting collaboration, and enabling a standard vulnerability tracking and management process.
The CVE system provides a standardized naming convention for security vulnerabilities, making it easier for security professionals, vendors, and researchers to discuss and share information about vulnerabilities. The centralized Database helps organizations track and manage security issues more effectively. Using CVE identifiers, different security tools and platforms can communicate more effectively, facilitating interoperability. Open tracking also encourages timely patching.
What information does a CVE contain?
CVE entries typically include details about the vulnerability, such as its severity, affected products and versions, technical descriptions, potential impact, and steps for mitigation or remediation. These entries serve as a valuable resource for security professionals to stay informed about the latest vulnerabilities and take appropriate actions to secure their systems and networks.
What is a Common Vulnerability Scoring System (CVSS)?
Common Vulnerability Scoring System (CVSS) is a standardized framework for assessing and communicating the severity of vulnerabilities in software and systems. CVSS provides a structured way to evaluate the potential impact and exploitability of a vulnerability, allowing organizations to prioritize their efforts in addressing security issues.
The CVSS framework assigns a numerical score to each vulnerability based on metrics that assess various aspects of the vulnerability’s impact and exploitability.
CVSS consists of four metric groups: Base, Threat, Environmental, and Supplemental. The CVSS Base Score is calculated based on several metrics related to the vulnerability’s exploitability and impact. These metrics include Attack Vector, Attack Complexity, Privileges Required, among others. Base metric values are combined with default values that assume the highest severity for Threat and Environmental metrics to produce a score ranging from 0 to 10.
A higher score indicates a more severe vulnerability. Examples of the CVSS can be viewed here.
What is the process for determining CVEs?
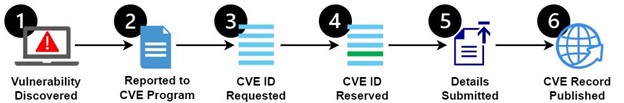
A vulnerability on the CVE List is associated with a CVE Record. When a vulnerability is discovered, the finder reports it through the CVE Program, to a CVE Program Partner. A CVE ID is reserved by the CVE Program Partner. If the vulnerability meets the minimum requirements for a CVE Record, it is confirmed and the record is published to the CVE List. CVE Records are published by CVE Program partners.
CVE Identifiers
A CVE identifier is a unique, standardized identifier assigned to a specific security vulnerability. Each CVE identifier consists of the prefix “CVE-” followed by a unique identifying number and possibly a year (e.g., CVE-2022-1234). This identifier allows security researchers, vendors, and organizations to reference and track vulnerabilities consistently across different systems and platforms.
Limitations of the CVE system
The CVE system has some limitations:
Coverage: The CVE system may not cover all vulnerabilities, especially those that are not publicly disclosed or those affecting less widely used software.
Delays: Assigning CVE identifiers does not happen immediately, particularly for less well-known vulnerabilities or those with lower severity levels.This can leave systems and users exposed to potential threats for longer periods.
Quality: The quality of CVE data can vary, as entries are often created by different individuals and organizations. In some cases, CVE entries may lack detailed information or contain inaccuracies.
Dependency: The CVE system relies on vulnerabilities being publicly disclosed to assign identifiers. This means that vulnerabilities discovered but not disclosed publicly may not receive CVE identifiers.
How does Acalvio ShadowPlex reduce CVE-related risks in digital environments?
Acalvio ShadowPlex uses Deception Technology. This involves deploying decoys and other deceptions that blend into the environment and lure attackers away from real assets. Since deception technology does not depend on attack signatures or other static indicators, it can detect a range of threats. Deception-based detection does not depend on whether the exploit has been seen before, so it does not matter if the assets on the network have any CVEs associated with them. ShadowPlex is capable of detecting even zero-day exploits, attacks that exploit vulnerabilities that do not have a CVE associated with them yet.
FAQs:
1. How is a CVE identified?
2. Who assigns CVE IDs?
3. How does the CVE system benefit organizations?
4. Where can I find information about specific CVEs?
The list of CVE Records is maintained on the CVE Website.